Log Streaming for Splunk Enterprise or Cloud
The Log Streaming service allows enriched logs from the USS platform to be streamed to external services such as SIEM solutions, analytics platforms and SoC services. To request access to the Log Streaming service, please contact your service provider.
- Log in to Splunk Enterprise or Cloud
- Navigate to Settings -> Data Inputs
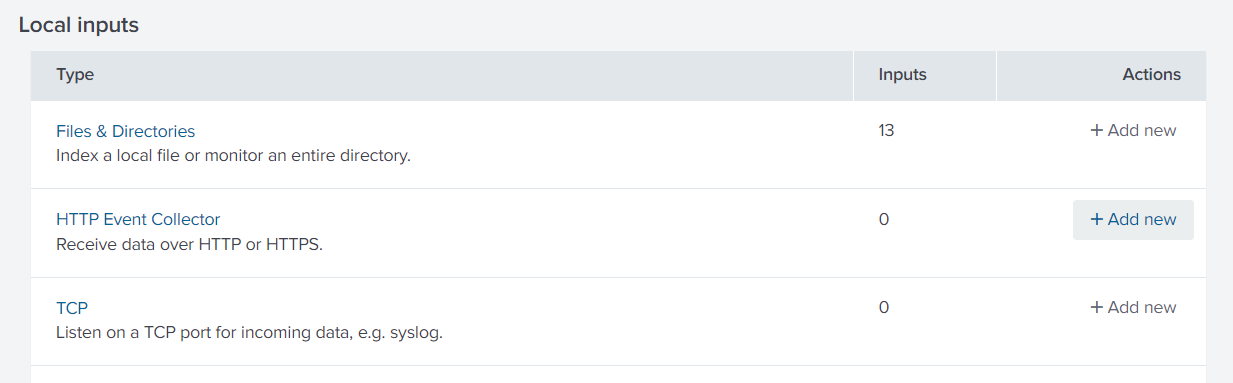
- Click Add New in the HTTP Event Collector row
- Enter a Name and click Next
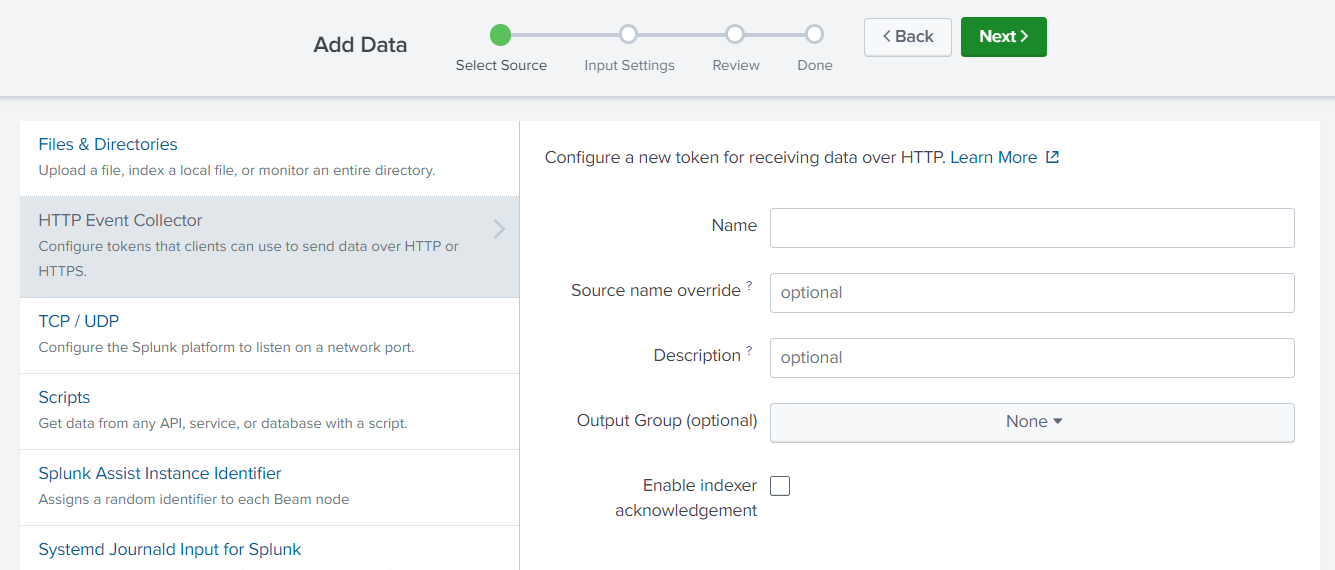
- Select an existing index or create a new one for the data and click Review
- Click Submit
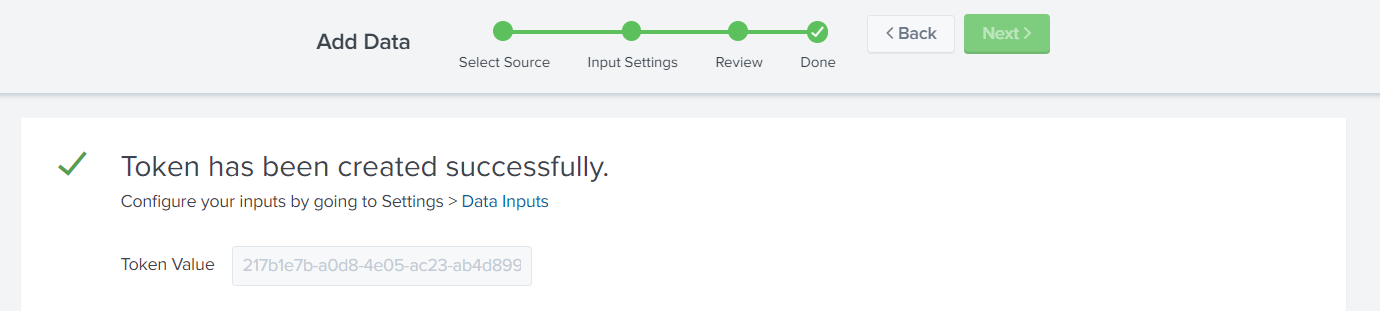
- Copy the Token Value and send it to your service provider along with your Splunk Enterprise Fully Qualified Domain Name (FQDN) where port 8088 is open for data ingest. Consult the Splunk installation documents for assistance with firewall configuration.
- Wait for confirmation from your service provider that the log stream has been configured
- Click Start Search or create a new search on the index used in Step 5
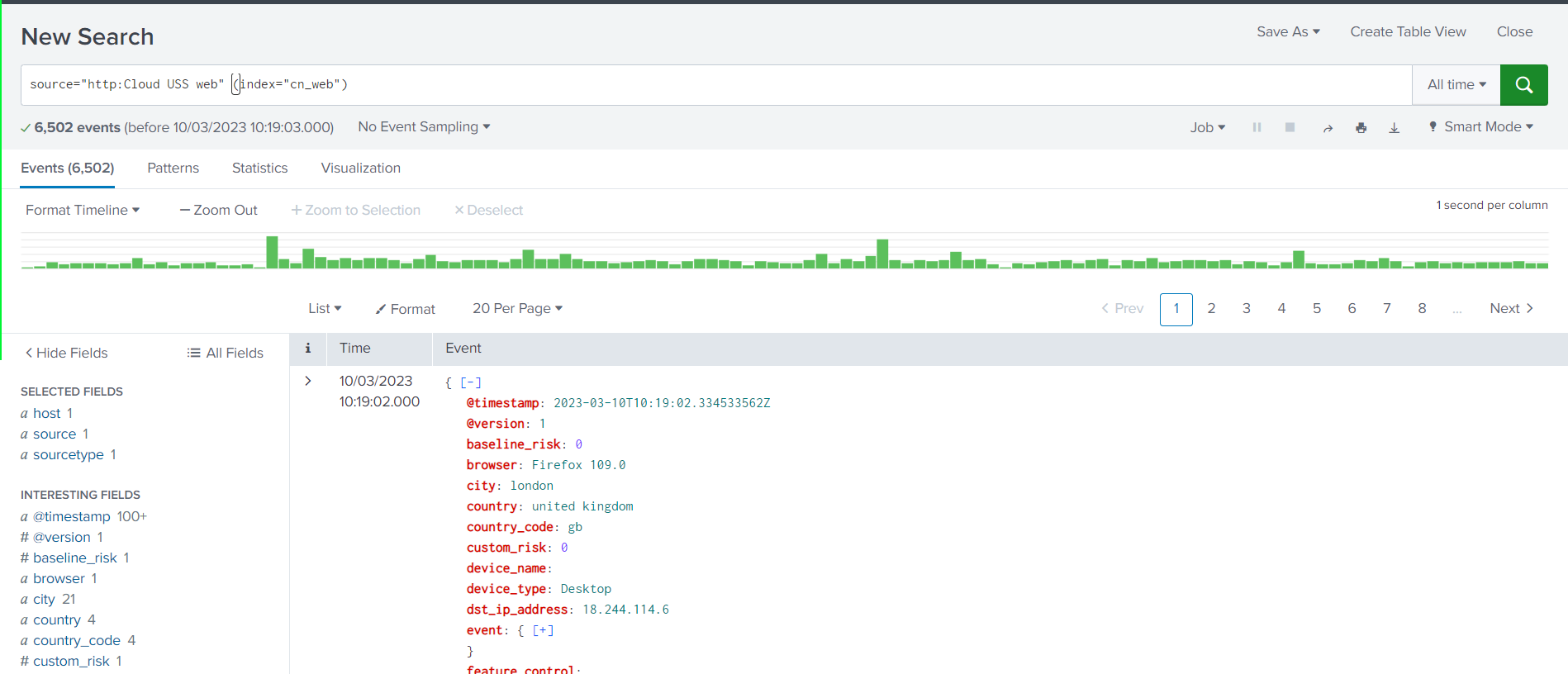
- The log stream is now set up and you can continue to query the data in Splunk Enterprise or Cloud.