Executive Tracking
This Rule detects "whaling" attacks. A whaling attack, sometimes called a "whale phishing" attack or CEO Fraud, is a specific type of phishing attack that targets high-profile employees such as the CEO or CFO. The intention of the attack is to steal sensitive information from a company (since employees that hold high positions within the company will tend to request other users to complete certain tasks on their behalf). In many such attacks, the attacker's goal is to manipulate the victim into authorizing high-value wire transfers to the attacker.
This Rule will Quarantine any emails that are suspected of being whaling attacks.
You can activate executive tracking for specific Active Directory groups on the Group Management screen.
To set up this Rule:
- Visit your USS Dashboard and click Products ⟶ E-mail Security ⟶ Message Rules.
- Click
 to create a new Rule.
to create a new Rule. - Give the Rule a sensible name, like "Executive Tracking", and click
 .
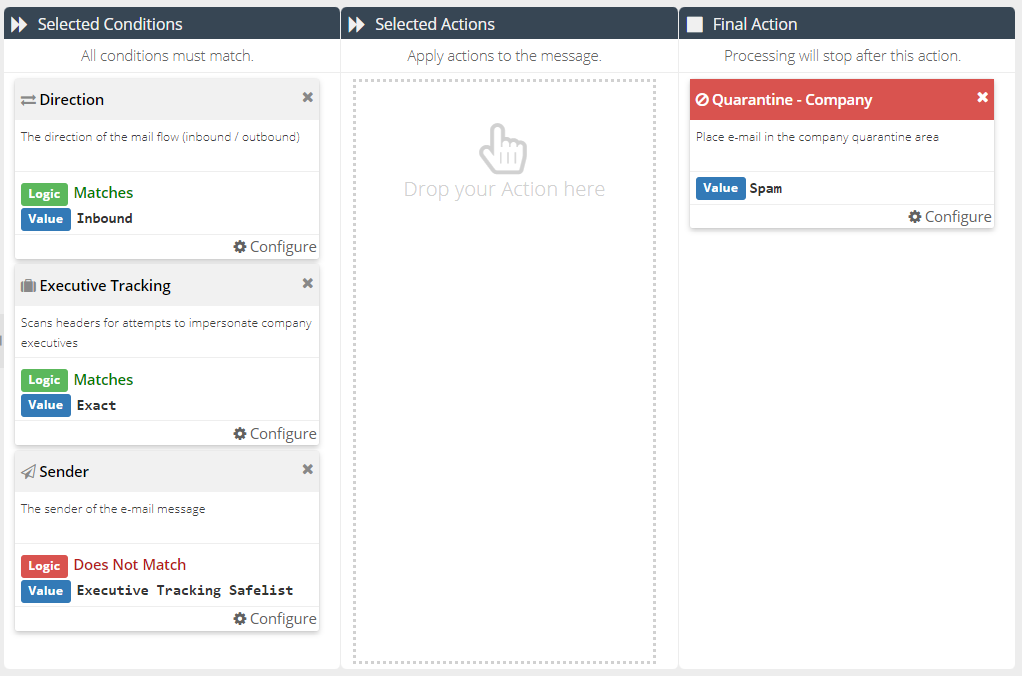
. - Add a Direction Condition, with the logic set to Matches: Inbound.
- Add an Executive Tracking Condition, with the value set to Matches: Contains.
- Add a Sender Condition, with the logic set to Does Not Match and then Executive Tracking Safelist (if this does not exist, you can create it in Custom Rule Data).
- Do not add any Actions.
- Add a Quarantine - Company Final Action, with the value set to Spam.
- Make sure that the Active checkbox is enabled, so that your new Rule will start working immediately.
- Click
 .
. - Drag the new Rule to a sensible position in your Message Rules window. If your Service Provider has set up your account with a set of default Rules, positioning this new Rule above the Deliver Inbound Rule is a good choice.
The completed Rule should look like this:
Condition Values
Contains | If the display name contains the selected users name or a configured variant. This is a wildcard match, for example “Mr. John Doe” and “John Doe Esq” would trigger if the first name and surname attributes were "John Doe" or if a variant of "John" was added. |
Exact | If the display name exactly matches the users first and last name or a configured variant. You must add a variant for every name you wish to detect. |
High | This option takes the first and last name and uses the Levenshtein Distance algorithm and Tanimoto Coefficient to automatically detect the similarity of the display name to the users real name. There is a risk of false positives associated with this option. |
Medium | This is a more relaxed version of the "High" option, therefore it will match more automatically calculated variants with less accuracy. There is a significant risk of false positives associated with this option. |
Excluding Email Addresses from Tracking
Navigate to Products -> Email Security -> Custom Rule Data and select the Executive Tracking Safelist entry. Add or update the Regular Expression so that it remains in this format, specifying multiple email addresses with a pipe | character.
^(addr1@domain\.com|addr2@domain\.com|addr3@domain\.com)$
Excluding Email Domains from Tracking
If you need to add entire domains in to the Regular Expression you can use the following format e.g. for domain1.com:
^(addr1@domain\.com|addr2@domain\.com|addr3@domain\.com)$|domain1\.com$|domain2\.com$