Active Directory and Entra ID
The Active Directory section allows you to configure synchronisation of one or more Active Directory domains with the USS cloud account. The advantage of this is that you can use Active Directory attributes in products that support them, such as Web Security, Email Security and Cloud Application Security. On-premise, Entra ID or hybrid environments are supported.
On-Premise Active Directory sync
To view and edit your User Directory syncs, visit your USS Dashboard and click Security Modules ⟶ User Directory.
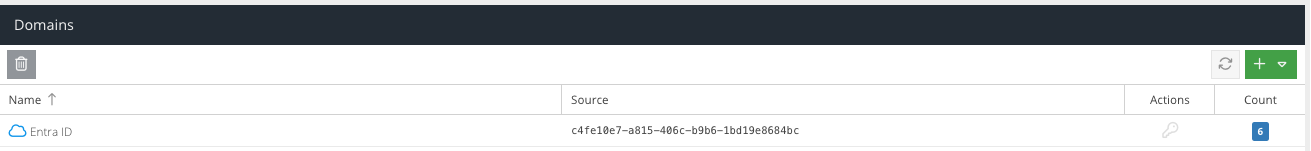
Your existing Active Directory listings will be shown. On-premise Active Directory connections have a Windows icon, and Entra ID Directory connections have a cloud icon.
To add a new domain connection, click the  button. Enter the details of your new domain into the form that's displayed.
button. Enter the details of your new domain into the form that's displayed.
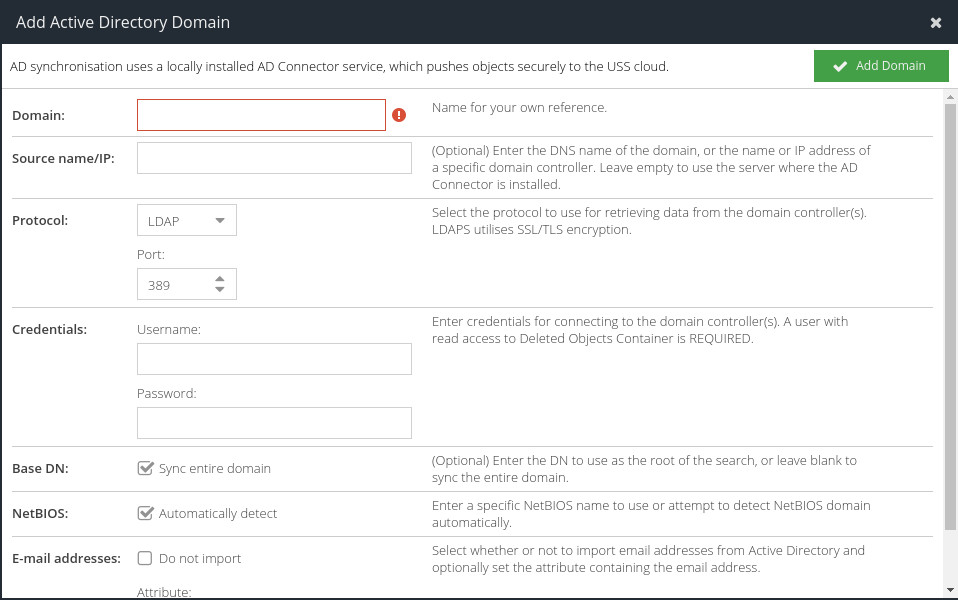
Options
Domain | A description for the domain. Typically your Active Directory domain name, for example: |
Server Hostname | Enter the DNS name of the domain, or the name or IP address of a specific domain controller. Enter |
Common Names | Only available if the Cloud MFA product is licensed. Synchronise the user common names as an alias, so that users can log in without needing to specify the domain of their username. |
MFA Users | Only available if the Cloud MFA product is licensed. This option will allow you to limit synchronising users to the Cloud MFA service based on group membership. Changing the MFA Group filter will cause existing users to be deleted, new users to be synchronised and Soft Tokens will require re-provisioning |
Protocol | Select the protocol to use for retrieving data from the domain controller(s). LDAPS utilises SSL/TLS encryption. |
Credentials | Enter credentials for connecting to the domain controller(s). A user with read access to Deleted Objects Container is recommended in order to remove objects from USS once they have been removed from Active Directory This can be entered in UPN format e.g. |
Base DN | Enter the DN to use as the root of the search, or leave blank to sync the entire domain. |
NetBIOS | Enter a specific NetBIOS name to use or attempt to detect NetBIOS domain automatically. |
Email Addresses | Select whether or not to import email addresses from Active Directory and optionally set the attribute containing the email address. |
Default Prefix | When importing phone numbers, this international dialling prefix will be used e.g. +1, +44 |
Phone numbers | Select whether or not to import phone numbers from Active Directory and optionally set the attribute containing the phone number. This is required for the MFA powered by IntelliTrust product. If enabled, the phone number field must contain a valid number. A leading zero is not permitted. |
Only synchronise users with this attribute set | This advanced option lets you specify an attribute I that must be present with the given value(s) in order for the user object to be synchronised. You may specify multiple values using a semi-colon |
Click  to add the domain to the list.
to add the domain to the list.
443 from the server the AD Connect agent is installed on, to the AD Connect web service.Optionally, create an API key pair to use with the AD Connect client software. If you do not create a key pair, you will need to authenticate with an administrator user and password with at least the Agent Installer role.
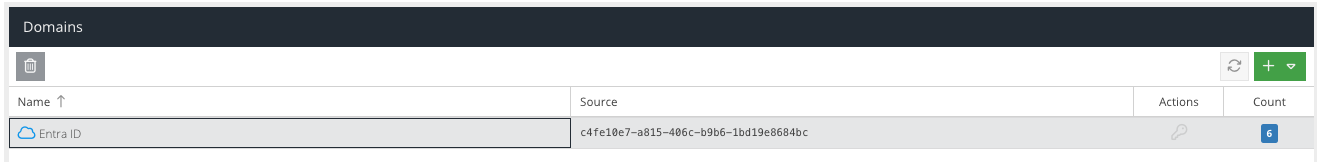
To create a key pair, after the new domain is added, click the key icon in the Actions column:
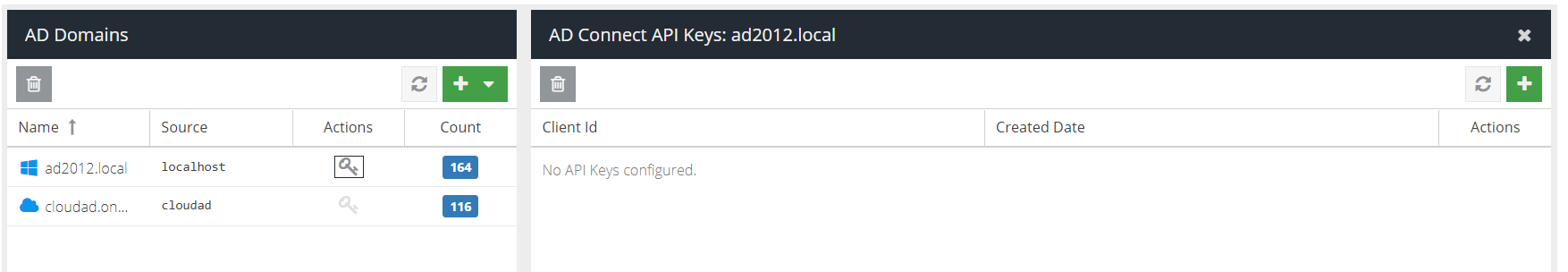
Click the + icon in the top right hand corner of the API Keys panel.
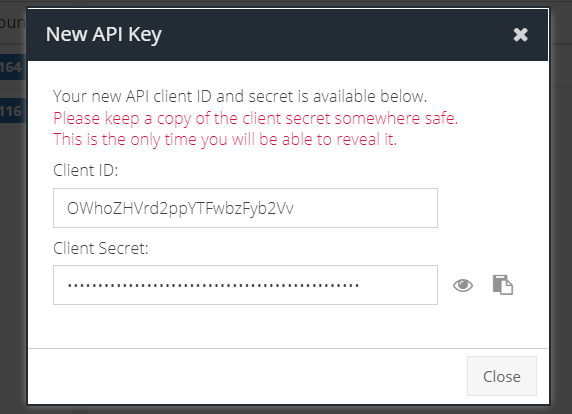
Copy the Client ID and Client Secret for use with the AD Connect client software.
You should now proceed to download and install the AD Connect software on your local network.
Entra ID / Hybrid Entra ID
You can link an Entra ID to USS, in addition to or instead of an on-premise Active Directory sync. To do so, select Microsoft Entra ID from the dropdown menu.
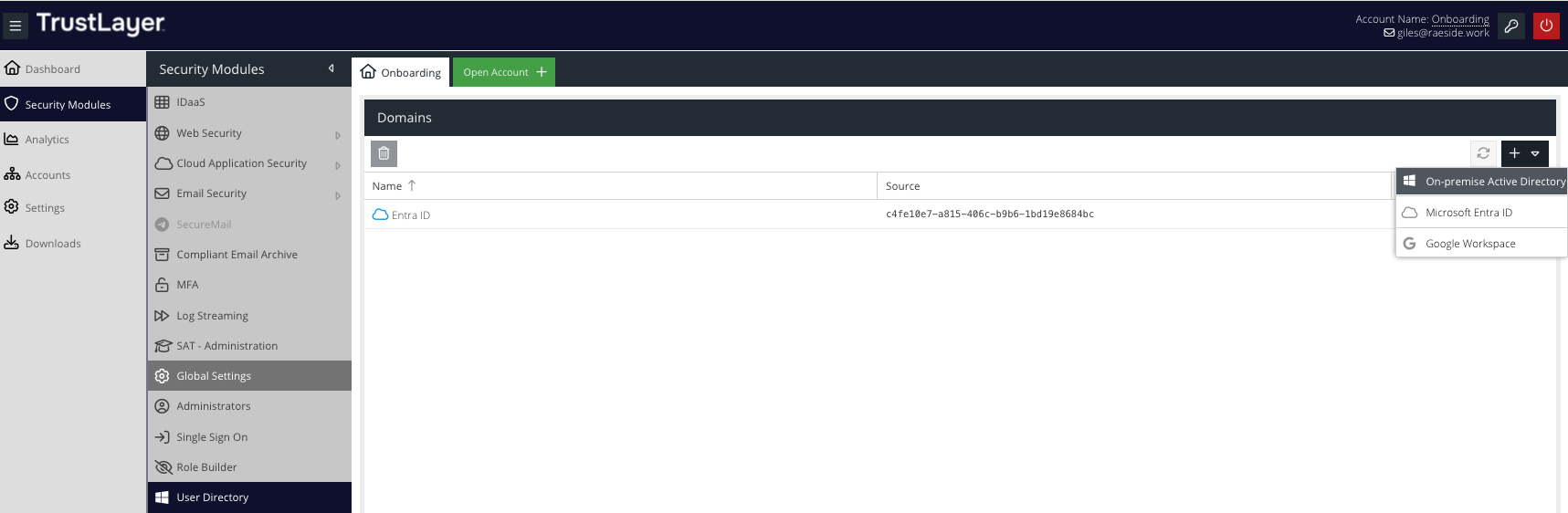
You will need your Entra tenant name (which will be in a form similar to name.onmicrosoft.com), and you'll be required to approve USS for read access to the Entra ID directory. You'll need an administrator account to grant that access.
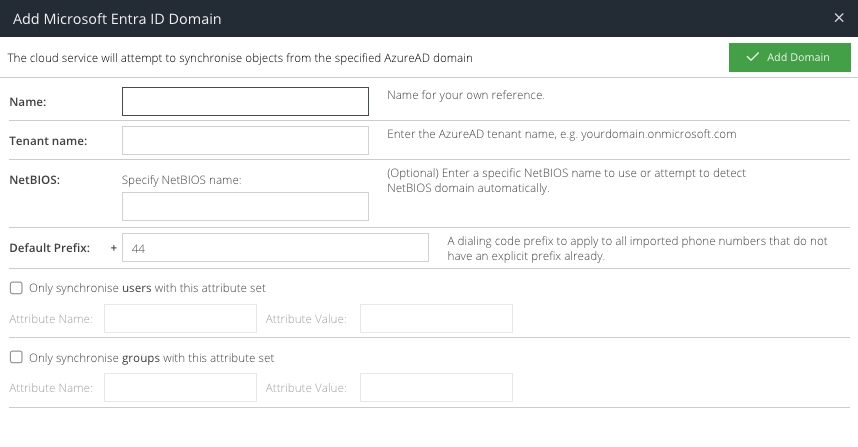
Options
Domain | This is a unique friendly name to identify the Entra ID connection. If using multiple domains, ensure the Domain name is unique. |
Tenant name | This is the Microsoft tenant name, e.g |
Common Names | Only available if the Cloud MFA product is licensed. Synchronise the user common names as an alias, so that users can log in without needing to specify the domain of their username. |
MFA Users | If the Cloud MFA product is license, this option will allow you to limit synchronising users to the Cloud MFA service based on group membership. Changing the MFA Group filter will cause existing users to be deleted, new users to be synchronised and Soft Tokens will require re-provisioning |
Email addresses | This option can be used to exclude email addresses from being synchronised. It is also possible to specify a custom attribute that contains the email address. Email addresses are used if the Cloud MFA product or Email Security product is licensed. |
Default Prefix | This specifies the default telephone prefix for synchronised users. This is required if the Cloud MFA product is licensed. |
Phone numbers | This option can be used to exclude phone numbers from being synchronised. It is also possible to specify a custom attribute that contains the phone number. Phone numbers are used if the Cloud MFA product is licensed. |
Only synchronise users with this attribute set | This advanced option lets you specify a User Property from the Graph API that must be present with the given value(s) in order for the user object to be synchronised. You may specify multiple values using a semi-colon |
Only synchronise groups with this attribute set | This advanced option lets you specify a Group Property from the Graph API that must be present with the given value(s) in order for the group object to be synchronised. You may specify multiple values using a semi-colon If you are using extended attributes, you will need to synchronise them with Entra ID using the Microsoft Entra ID Directory Connect tool. |
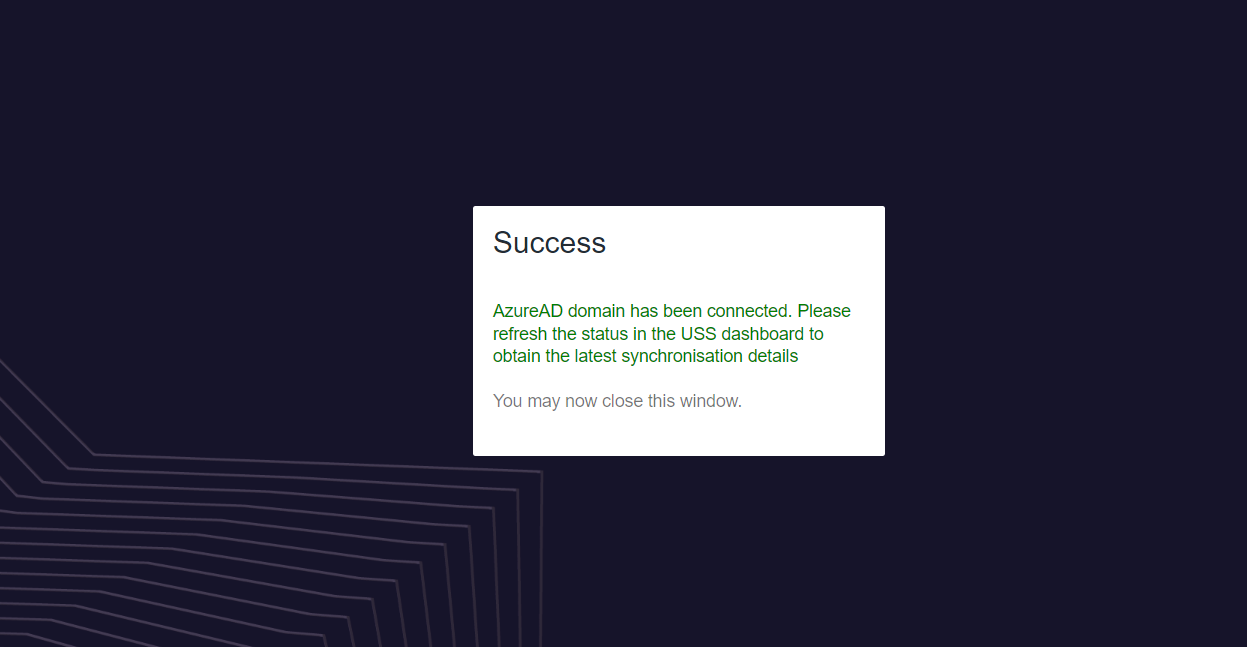
Once the domain is added, a new browser window will open and redirect you to Microsoft login page for the specified tenant in the Tenant Name option.
You must sign in with an administrator account for the tenant and grant consent for the USS service to read directory data from Entra ID.
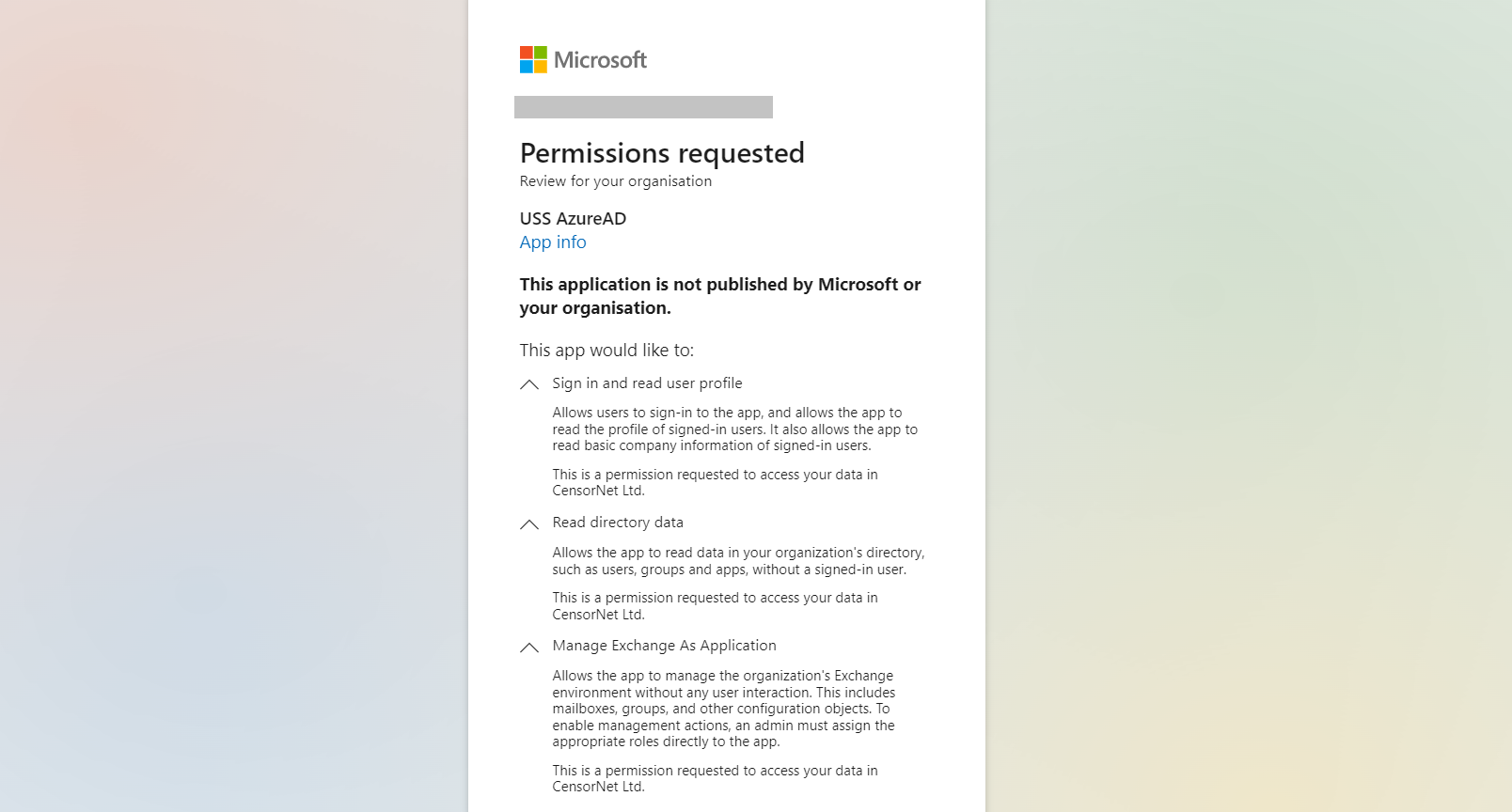
The permissions are as follows:
Permission | Description | API Permission (see reference) | Why is it needed? |
Sign in and read user profile | Allows users to sign-in to the app, and allows the app to read the profile of signed-in users. It also allows the app to read basic company information of signed-in users. | User.Read | To authenticate the administrator, verify the tenant details and ensure there is permission to create the USS Entra ID Enterprise app. |
Read directory data | Allows the app to read data in your organization's directory, such as users, groups and apps. | Directory.Read.All | To access all Entra ID objects with read only permission, in order to synchronise them with the USS dashboard. No credentials are transferred. |
Manage Exchange As Application | Allows the app to manage the organization's Exchange environment without any user interaction. This includes mailboxes, groups, and other configuration objects. To enable management actions, an admin must assign the appropriate roles directly to the app. | Exchange.ManageAsApp | To simplify the configuration of Shared Mailbox detection. This permission alone does not grant any access other than to be able to send Graph API requests, which by default will be denied until further permissions are added manually via the Entra Portal. This permission can be removed from Enterprise Apps -> USS Entra ID -> Permissions section if Shared Mailbox detection is not required. |
Click Accept to continue. You can now close the browser tab and return to the USS dashboard.