Configuring RD Web Access using IIS Website Protection
This document is intended for the Cloud MFA administrators.
Protection of RD Web Access using IIS Website Protection
This section describes how to protect the Remote Desktop Web Access Site on a Windows Server 2008 R2 / 2012 R2 / 2016 / 2019.
- The SMS PASSCODE IIS Website Protection component must be installed on the Web Server (i.e. the RD Web Access server). You may install any other SMS PASSCODE components on the Web Server as well.
- It is mandatory, that the RD Web Access site and RD Gateway site reside on the same server.
- Please note:
- Single sign-on in the RD Web Access site is supported.
- Accessing RemoteApps through the RD Web Feed is not supported.
- If the “Password Change” feature is enabled in the RD Web Access Site, then the “Password change” site is NOT protected by multi-factor authentication. Consequently, users will be able to change their password without a multi-factor authentication (but are always forced to perform MFA before accessing any RemoteApps).
- Specific for Windows Server 2012 R2 / 2016 / 2019: Only RDP Clients version 8.1 and later are supported. Access via older RDP Clients will be denied access. RDP Client 8.1 is supported on Windows 7 SP1 and later
In the subsections below you will find detailed instructions regarding the required setup to protect your RD Web Access Site. In both subsections, the term “Web Server” refers to the corresponding server in the network diagram above (the server with both the RD Web Access Site and RD Gateway installed).
Protecting RD Web Access (Windows Server 2008 R2)
To protect the RD Web Access Site using SMS PASSCODE multi-factor authentication on a Windows Server 2008 R2, please follow the instructions below:
- Set up the Web Server if this has not been done yet. I.e. install IIS, RD Web Access Site and RD Gateway on the Web Server. Do NOT install SMS PASSCODE IIS Website Protection on the Web Server yet.
- Test and verify that remote access (from the external network) to RemoteApps through the RD Web Access Site works as expected (using only AD credentials for authentication). If you are planning to use single sign-on (SSO):
- Test and verify that SSO works as expected.
- It is strongly recommended, when using SSO, to update the
renderscripts.jsfile on the RD Web Access Site. To do this, on the server hosting the RD Web Access site go to http://support.microsoft.com/kb/977507 and click the “Fix it” button on this page. This will update therenderscripts.jsfile.
- You are now ready to add SMS PASSCODE protection as described in the steps below. Enter the following two lines into the Custom RDP settings textbox:
pre-authentication server address:s:https://fqdn/rdroot
require pre-authentication:i:1
where fqdn must be replaced with the fully qualified domain name of the SSL certificate used for publishing the RD Web Access site, and rdroot must be replaced with the RD Web Access URL (“RDWeb” by default).
- Now, install SMS PASSCODE IIS Website Protection on the Web Server. During the installation, enable SMS PASSCODE protection of the RD Web Access Site:
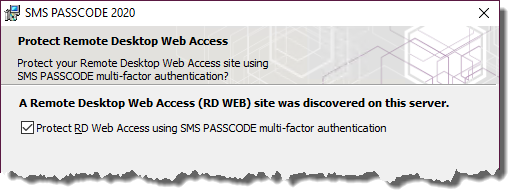
- Test that SMS PASSCODE authentication works as expected.
This completes the procedure for protecting the RD Web Access Site on a Windows Server 2008 R2, using SMS PASSCODE multi-factor authentication.
Protection of RD Web Desktops using IIS Website Protection (Windows Server 2008 R2)
On a Windows Server 2008 R2, if you have protected the RD Web Access Site using SMS PASSCODE IIS Website Protection as described in the previous section, and you are making use of the RD Web Remote Desktop feature (accessing full desktops of internal machines through the RD Gateway):
Please follow the procedure below, performing the specified actions on the server hosting the RD Web Access Site:
- Make a backup of the following file:
C:\Windows\Web\RDWeb\en-US\desktops.aspx - Now edit the original
desktops.aspxfile, and search for the text “authentication level”. Replace the line:
RDPstr += "authentication level:i:2\n";
with:
RDPstr += "require pre-authentication:i:1\n";
RDPstr += "pre-authentication server address: s: https://fqdn/rdroot\n";
where fqdn must be replaced with the fully qualified domain name of the SSL certificate used for publishing the RD Web Access site, and rdroot must be replaced with the RD Web Access URL (“RDWeb” by default).
- Save the changes to the
desktops.aspxfile - Test that Remote Desktops can be accessed through the SMS PASSCODE protected RD Web Access Site
Protecting RD Web Access (Windows Server 2012 R2 / 2016 / 2019)
To protect the RD Web Access Site using SMS PASSCODE multi-factor authentication on a Windows Server 2012 R2 / 2016 / 2019, please follow the instructions below:
- Set up the Web Server if this has not been done yet. I.e. install IIS, RD Web Access Site and RD Gateway on the Web Server. Do NOT install SMS PASSCODE IIS Website Protection on the Web Server yet.
- Test and verify that remote access (from the external network) to RemoteApps through the RD Web Access Site works as expected (using only AD credentials for authentication). If you are planning to use single sign-on (SSO), then please also test and verify that SSO works as expected.
- Now, install SMS PASSCODE IIS Website Protection on the Web Server. During the installation, enable SMS PASSCODE protection of the RD Web Access Site:
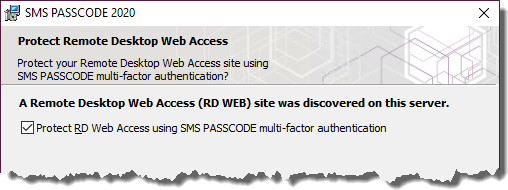
smspasscodelogon site is installed as per the screen below, if not please see section “Powershell Commands”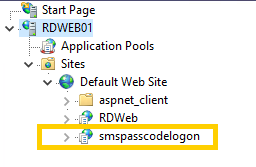
- Test that SMS PASSCODE authentication works as expected
- On Windows Server 2012 R2, if multi-factor authentication works, when accessing the RD Web Access site, but starting RemoteApps fails with the error message "This RDP File is corrupted. The remote connection cannot be started" then please read section “RD Web Protect trouble shooting” for solving this issue
- On Windows Server 2016 / 2019, if single sign-on (SSO) does not work, meaning the user has to re-authenticate on the RD Session Host, then please read section “RD Web Protect trouble shooting”for solving this issue
This completes the procedure for protecting the RD Web Access Site on a Windows Server 2012 R2 / 2016 / 2019, using SMS PASSCODE multi-factor authentication.
PowerShell Commands
To enable SMS PASSCODE authentication for a specific website, use the Protect-SmsPcIisWebSite command in one of the following two ways:
To enable for RdWeb only run the below command
Protect-SmsPcIisWebSite –Name “Default Web Site” -RdWeb
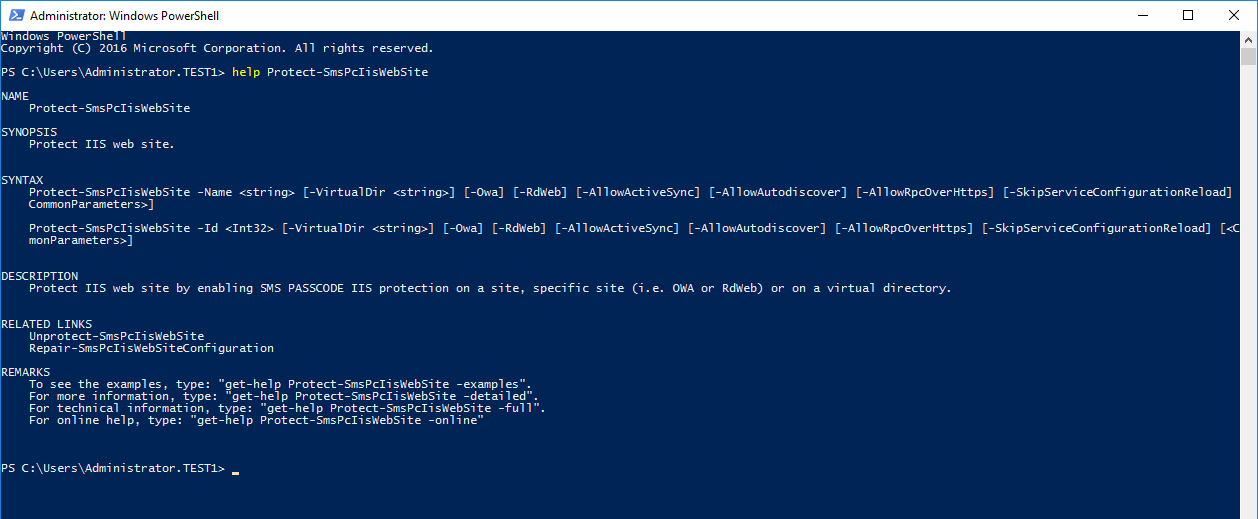
The different arguments of the command are described in the table below.
Argument | Description |
-Name | This argument is used to specify the name of the website to protect. Example: |
-Id | This argument is used to specify the IIS ID of the website to protect. The default website always has ID 1. Example: Use IIS administration PowerShell module command ( |
-VirtualDir (optional) | This optional argument is used to specify the name of the virtual directory under the website. Only this virtual directory will be protected. Example: |
-Owa (optional) | This argument is required if the website is an OWA Website using form- based authentication. For websites using Basic or Integrated Windows Authentication, please omit this argument. |
-AllowActiveSync (optional) | This argument is only allowed together with the -Owa argument. It instructs the HTTP module to disable SMS PASSCODE authentication for ActiveSync connections. |
-AllowAutoDiscover (optional) | This argument is only allowed together with the -Owa argument. It instructs the HTTP module to disable SMS PASSCODE authentication for ActiveSync AutoDiscover requests. |
-AllowRpcOverHttps (optional) | This argument is only allowed together with the -Owa or -RdWeb arguments. It instructs the HTTP module to disable SMS PASSCODE authentication for RPC over HTTP/HTTPS connections. |
-RdWeb | This argument is required if the website is an RD Web Access site using form-based authentication. For websites using Basic or Integrated Windows Authentication, please omit this argument. |
RD Web Protect Troubleshooting
If signing of RDP files is enabled on your RD Web Access server, you might experience issues with your SMS PASSCODE protected RD Web site. The symptoms are:
- Windows Server 2012 R2: Starting RemoteApps from the RD Web site fails with the error message “This RDP File is corrupted. The remote connection cannot be started.”
- Windows Server 2016/2019: When starting RemoteApps, users need to re-authenticate on the RD Session Host (single sign-on not working).
If above applies to your installation, you need to re-configure your RD session collection. This is accomplished by executing the following PowerShell commands on the RD Web Access server:
Import-Module RemoteDesktop
Get-RDSessionCollection | Set-RDSessionCollectionConfiguration -CustomRdpProperty "gatewaycredentialssource:i:5"
Thereafter, users should be able to start RemoteApps from the RD Web Access site.
If you later on need to revert the re-configuration of the RD session collection, this is accomplished by executing the following PowerShell commands on the RD Web Access server:
Import-Module RemoteDesktop
Get-RDSessionCollection | Set-RDSessionCollectionConfiguration -CustomRdpProperty "`n"