Connector Mode Setup
Connector Mode is an alternative mail delivery method to using DNS based MX record redirection. It provides a quick and easy onboarding process for the Email Security product and provides additional capabilities such as a consolidated email quarantine within Microsoft 365.
Enable-OrganizationCustomization. Please wait a little longer and then try again.Connector Mode Step-by-Step Guide
To set up the Connector Mode, follow the steps below:
- Visit the Security Modules -> Email Security -> Product Configuration -> Domains
If you are setting up Email Security for the first time, you will be prompted to select the desired mode. If you are a Microsoft 365 customer, click the Connector Mode tile and continue with this guide.
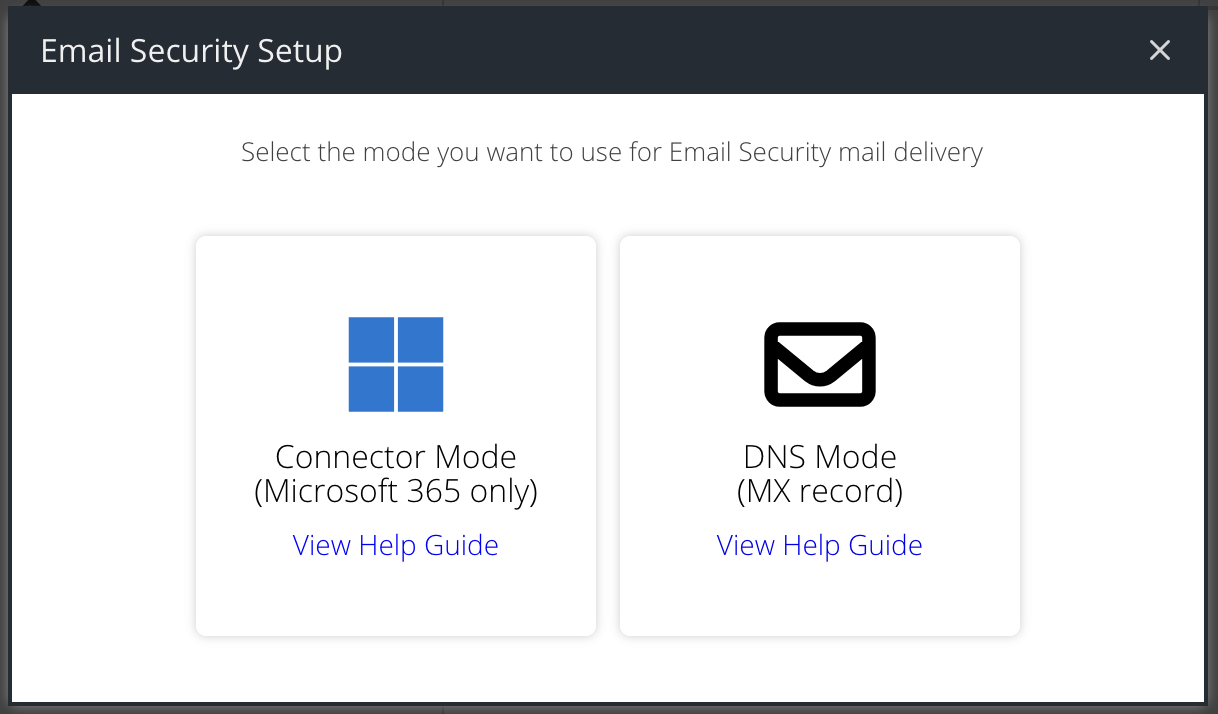
If you are an existing customer and have MX record mode configured, but want to migrate to Connector Mode then you can click the Migrate to Connector Mode button:
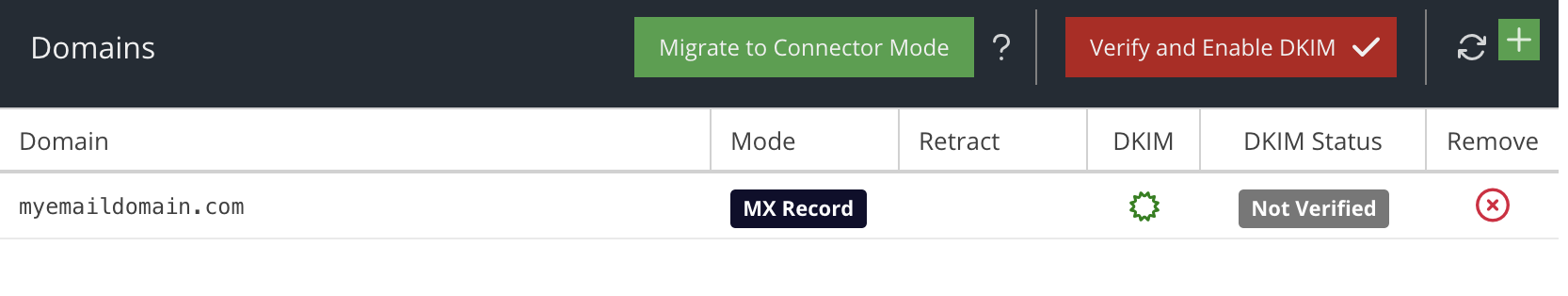
- The Connector Mode wizard will open in a new browser window.
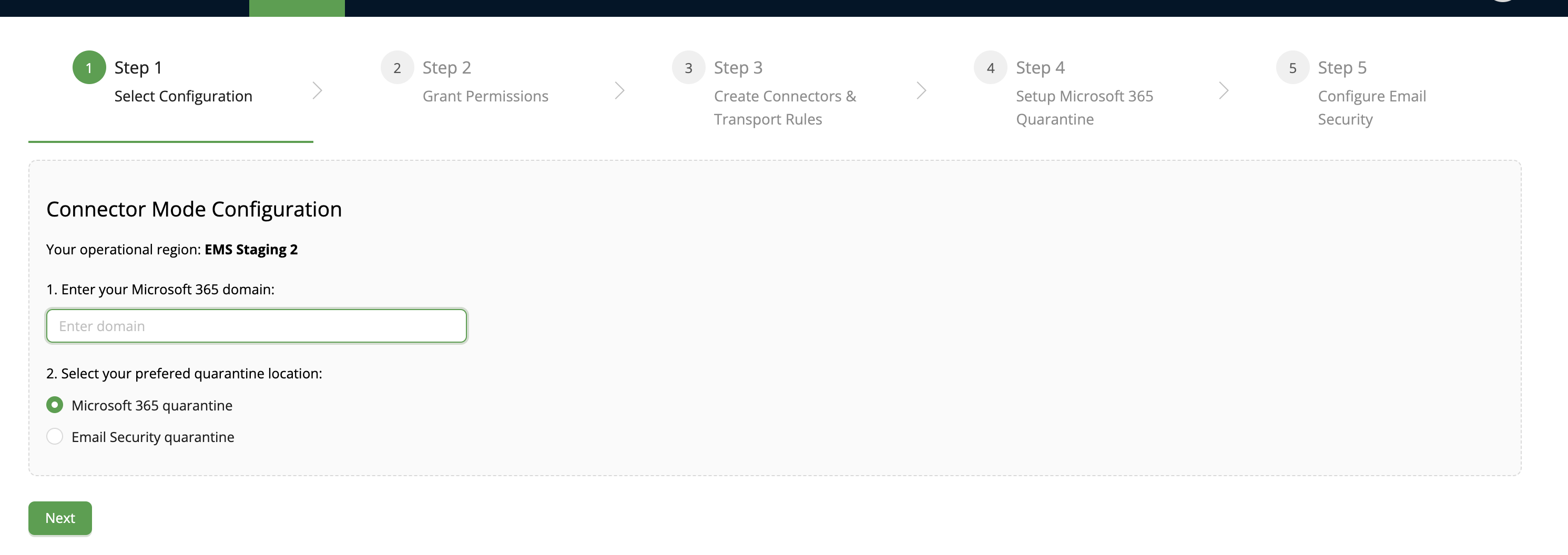
- Provide the Microsoft 365 domain you want to connect to the Email Security system. It should be a domain you use for email exchange.
- The domain you enter must have its MX records pointing to Microsoft 365. If you have an existing domain and are migrating to Connector Mode, we recommend you contact your Service Provider to discuss the process first.
- If you receive a Permission Error make sure you are signed out of any Microsoft 365 accounts that do not relate to the domain you have chosen.
- Select the quarantine type that you would like to use. Two quarantine types are available now:
- Default Email Security Quarantine: All emails scanned by the Email Security system and processed by the Quarantines action are sent to the Global Quarantine within the dashboard. This fully supports Global and Personal (end-user) quarantines.
- Microsoft 365 Quarantine: All emails scanned by the Email Security system and processed by the Quarantine actions are sent to the Quarantine within Microsoft 365. You can manage such emails via the Microsoft Defender portal in the same way as emails quarantined by Microsoft 365. This uses a special header to identify Quarantined email from the Email Security product and a Transport rule (see table below) recognises this and redirects it to the Microsoft 365 quarantine. See the note at the end of the article about TERRL limits.
- You will be redirected to the Microsoft Permission Request page to grant the required permission for the Connector Mode application.The Permission Request will be sent only during the first Connector Mode setup. For the reset action (removing Connector Mode), it will be skipped as long as all required permissions have already been granted.
- Click the Accept button and you will be redirected back to the Connector Mode wizard. The Email Security system will register the Connector Mode application within Microsoft Entra ID and assign the Exchange Administrator role.
- Confirm the creation of the required connectors and the transport rules. The Email Security system will create the following connectors and transport rules in your Microsoft 365 account.
Connector | Description |
Email Security (clouduss.com) to M365 | Emails will be resent from the Email Security inbound server to the Microsoft 365 server. |
M365 to Email Security (clouduss.com) Outbound | Emails will be resent from the Microsoft 365 server to the Email Security inbound server. Disabled by default - see note on Outbound below |
M365 to Email Security (clouduss.com) Inbound | Emails will be resent from the Microsoft 365 server to the Email Security outbound server. |
Email Security (clouduss.com) Outbound to M365 Quarantine | Outbound emails that have triggered rules with Quarantine actions will be resent from the Email Security outbound server to the Microsoft 365 server. |
Transport Rule | Description | What it does |
Email Security (clouduss.com) Allow List | It reset the spam confidence level (SCL) to -1 for all emails sent from the Email Security servers. | It checks that an email comes from one of the Email Security IP addresses, and, sets the SCL to -1 for this email. |
Email Security (clouduss.com) Inbound Mail Protection | It triggers if an email comes from outside the organisation (domain). | It uses the M365 to Email Security (clouduss.com) Inbound connector to take an email from the Microsoft 365 server to the Email Security inbound server. Also, it adds the Email is tagged with |
Email Security (clouduss.com) Outbound Mail Protection | It triggers if an email goes from inside the organisation to an external domain. | It uses M365 to Email Security (clouduss.com) Outbound to send an email from the Microsoft 365 server to the Email Security outbound server. Also, it adds the |
Email Security (clouduss.com) Internal Mail Protection | It triggers if an email is sent from one user to another user within the organisation. | The same as for Email Security (clouduss.com) Inbound Mail Protection transport rule. (not active as part of Early Access) |
Email Security (clouduss.com) - End-User Quarantine | It redirects the quarantined emails to the Microsoft end-user quarantine if the Microsoft 365 Quarantine option is selected. | It checks that an email originates from one of the Email Security IP addresses, and the |
Email Security (clouduss.com) - Admin Quarantine | It redirects the quarantined emails to the Microsoft admin quarantine if the Microsoft 365 Quarantine option is selected. | It checks that an email originates from one of the Email Security IP addresses, and the |
- Optionally, you can review your Connector and Transport rules within Microsoft 365 using the following links:
- Connector Rules: https://admin.exchange.microsoft.com/#/connectors
- Transport Rules: https://admin.exchange.microsoft.com/#/transportrules
- If you have selected the Microsoft 365 Quarantine, confirm the creation of the Quarantine Policy, the Anti-Spam Policy, and Quarantine Transport rules as part of the installation process
- The Email Security system will finish the Connector Mode configuration by performing an automated configuration of the Email Security product. For reference, these steps are described below:
- Adds the domain name and the Exchange email server address for delivery to Security Modules -> Email Security -> Domains
- Creates a new M365 Domain custom rule data with the Microsoft 365 domain value in Security Modules -> Email Security -> Custom Rule Data
- Creates a new TLS Enforced rule in Security Modules -> Email Security -> Message Rules
- If the Microsoft 365 Quarantine option is selected, replace Email Security quarantine actions with the corresponding actions for Microsoft 365 quarantine
- When the automatic configuration is finished, configure automatic synchronisation of your organisation’s mailboxes (email addresses) using Active Directory or Entra ID. Follow this guide for instructions.
- Add the SPF record provided to your domain. Assuming your domain is registered with Microsoft, please follow these steps. If your domain is hosted elsewhere, consult your Domain Registrar instructions for adding an SPF record.
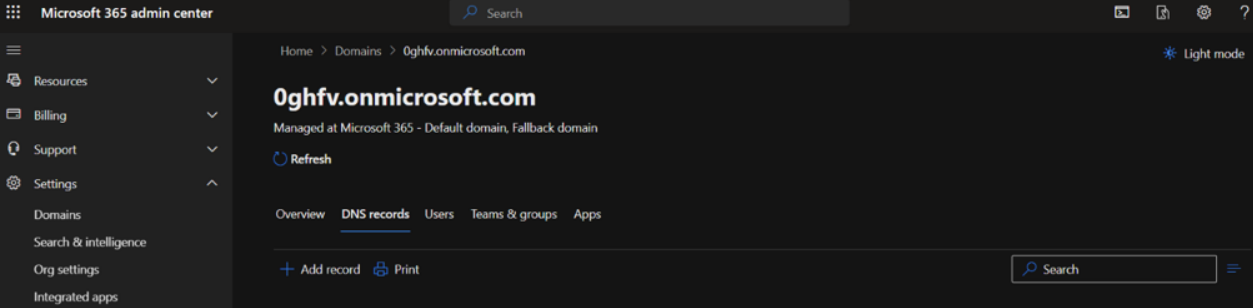
- Visit the Microsoft 365 Admin Center -> Domains
- Select the domain you have configured with the Connector Mode wizard and navigate to the DNS records tab:
- Add the SPF record to your DNS record in the following format:
Copy the suggested SPF record from the Connector Mode setup dashboard. Without this record, destination SMTP servers can reject emails coming from the Email Security MTA servers.
v=spf1 xx.xx.xx.xx include:spf.protection.outlook.com -allWhere xx.xx.xx.xx is your outgoing SMTP server IP address.
- The Connector Mode setup is now complete
Removing Connector Mode
If you wish to remove the Connector Mode, follow these steps:
- Navigate to Security Modules -> Email Security -> Product Configuration -> Domains
- Click the Reconfigure Connector Mode button
- The Connector Mode uninstall wizard opens in a new tab
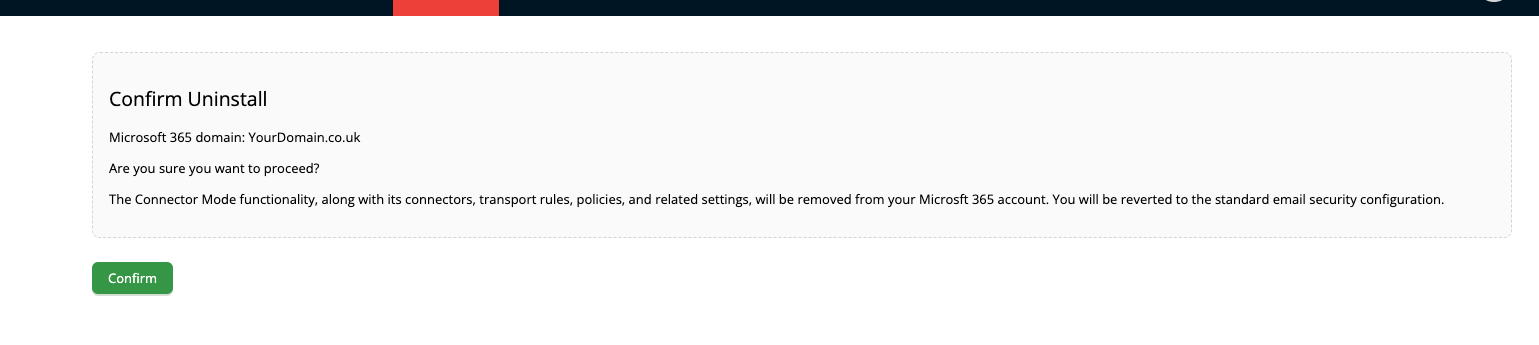
- Details for the configured domain will be shown. Click confirm and the configuration will be removed
- Email flow will return to the standard Microsoft 365 delivery rules. If you wish to return to DNS based MX record mode with Email Security, please follow the Getting Started guide.
Video Guide
The video below will walk you through the steps to set up connector mode.
Outbound Email Flow and Tenant External Recipient Rate Limit (TERRL)
Enabling outbound email protection rules will send quarantined messages back to Microsoft 365 so those recipients will be counted twice against the TERRL quota (both tenant and mailbox). This only applies if you are using the unified Microsoft 365 Quarantine option.
For further information on TERRL please see the Microsoft article (external link).