Unable to forward emails from Microsoft 365 accounts
If you are having issues with forwarding emails from Microsoft 365 accounts and you are receiving the following errors, this article discusses possible solutions depending on your configuration.
550 5.4.300 Message expired -> 421 4.4.0 Remote server response was not RFC conformant
550 5.0.1 Unable to Relay
Microsoft Office 365 supports Sender Rewriting Scheme (SRS), as per the following Microsoft Article: https://learn.microsoft.com/en-us/exchange/reference/sender-rewriting-scheme (external link)
Without SRS emails will be rejected. Although the Email Security service knows the IP Address is part of the SPF record an will know it has originated from Microsoft 365, the systems also needs to be able to assign it to an account and this is why we have implemented additional authentication for the SMTP From and From addresses, as per the following article:
https://help.clouduss.com/ems-knowledge-base/unable-to-relay-error-on-outbound-email
Without the additional authentication, an open relay would exist, allowing malicious actors to use the email service to potentially deliver spam emails.
There are 3 optional solutions depending on your service’s configuration to resolve these mail-forward delivery issues.
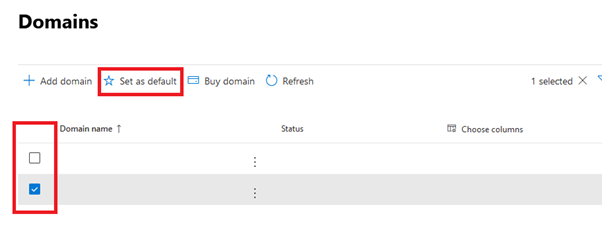
- Check your default domain in Microsoft 365:
The first solution is to check your default domain and make sure that your external domain is set as the default. You can find this by navigating to the following Microsoft 365 section: https://admin.microsoft.com/Adminportal/Home?#/Domains (external link)
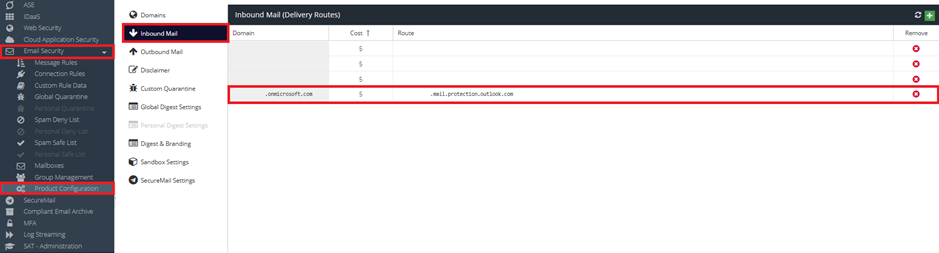
- Add your onmicrosoft.com domain with the default route to the list of Email Security domains:
Log in to the dashboard and navigate to Email Security -> Product Configuration -> Domains
Add a new domain that matches the domain section from Microsoft 365 and add a domain route accordingly e.g. <your domain-TLD>.mail.protection.outlook.com.
- Bypass Email Security for Forwarded Addresses
This is a final option, if you are unable to configure domains within Microsoft 365 or the Email Security service. You can create a rule and a connection policy that bypasses Email Security for Forwarded Addresses.
Firstly, log in to your Exchange Admin Console with an Administrator Account, you can use the following link:
https://admin.exchange.microsoft.com/#/homepage (external link)
Navigate to Connectors, and click Add a connector, then use the following process:
Select Office 365 under "Connection From"
Select Partner Organization under "Connection to"
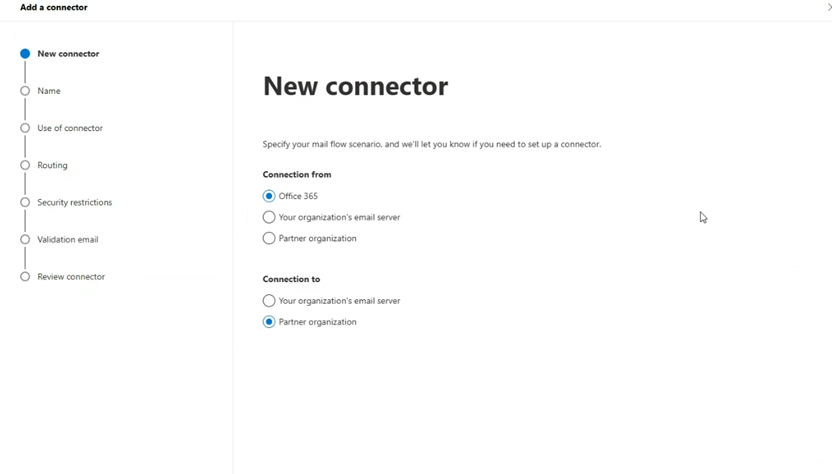
Select Next
Give the Connector a friendly name and description for your own identification and optionally add a description.
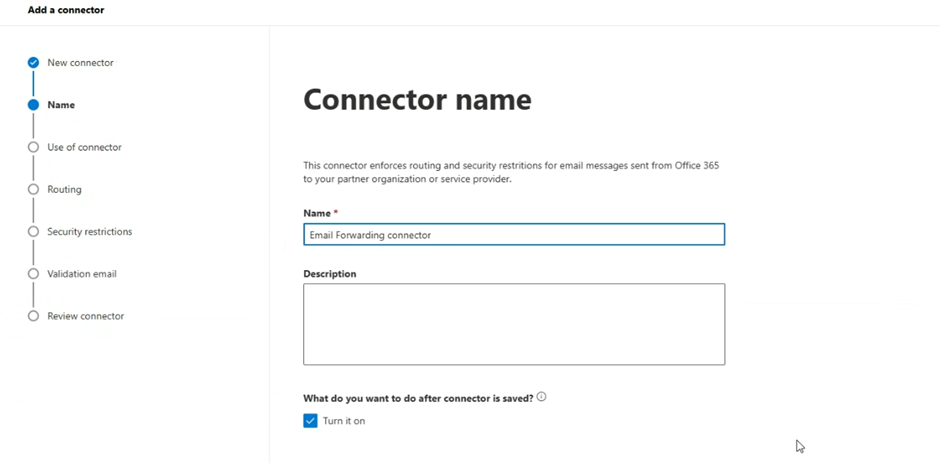
Select Next
Select Only when I have a transport rule set up that redirects messages to this connector
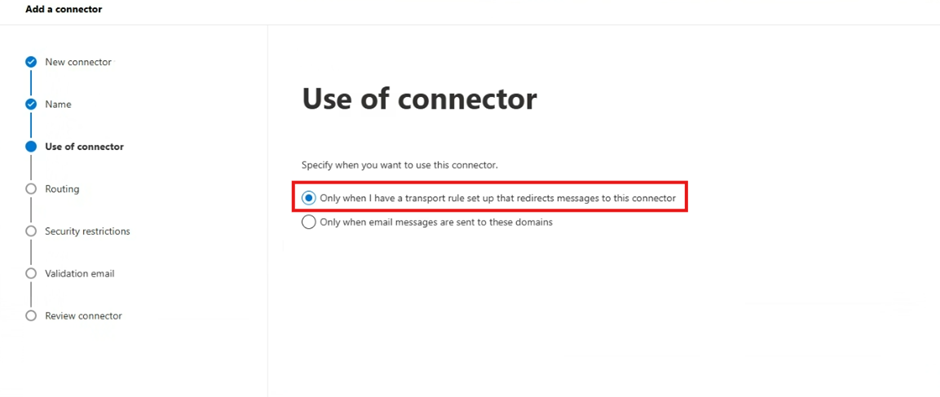
Select Next
For Routing, select Use the MX record associated with the partner’s domain
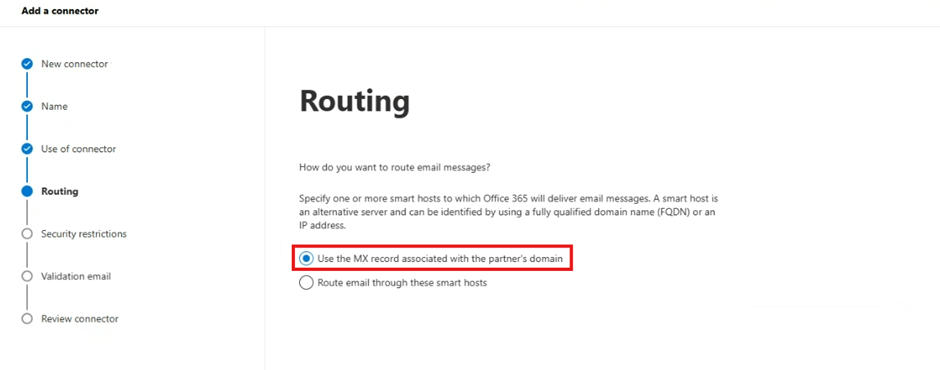
Select Next
Select the defaults in the Security Restrictions section
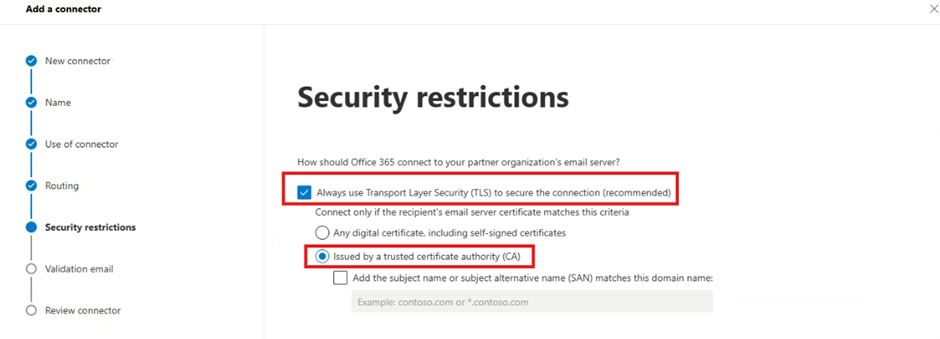
Select Next
Enter the forwarding address that are being forwarded to and click Validate
This adddress MUST be an external address that you have access to, for example a gmail.com address.
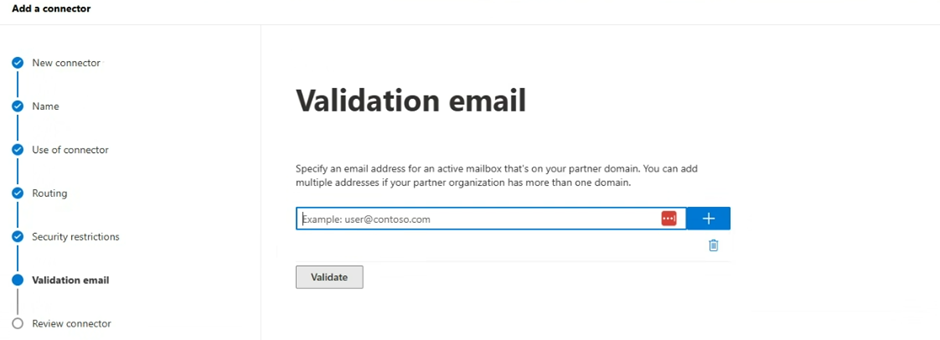
The validation process will start and this will send a test email automatically to the configured address to verify delivery. Please check you have received it.
Select Next
Review the connector configurations and click Create Connector.
Navigate to Rules within the Exchange Admin Console, and click Add a rule -> Create a new rule:
Enter the following configuration;
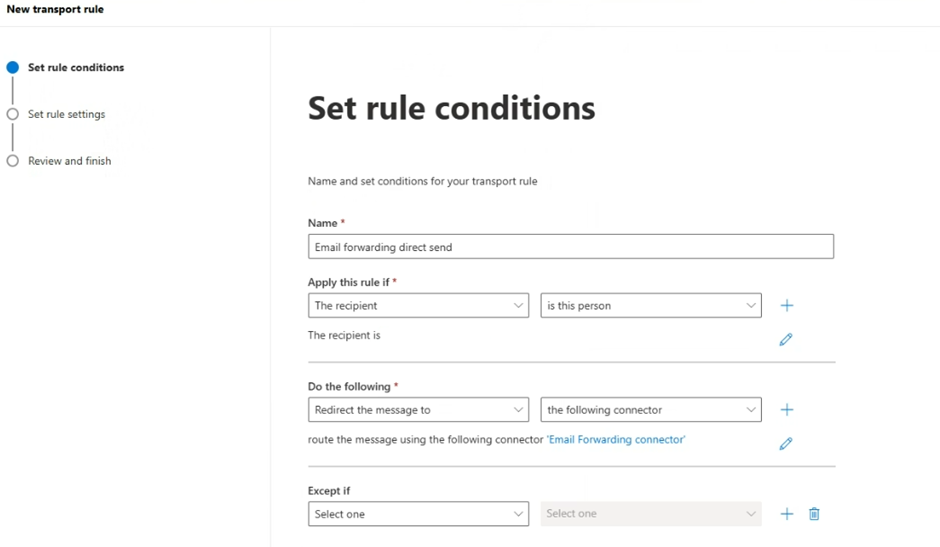
Select Next
Set rule conditions to make sure that the Rule Mode is set to Enforce, and the tick box for Stop processing more rules is enabled
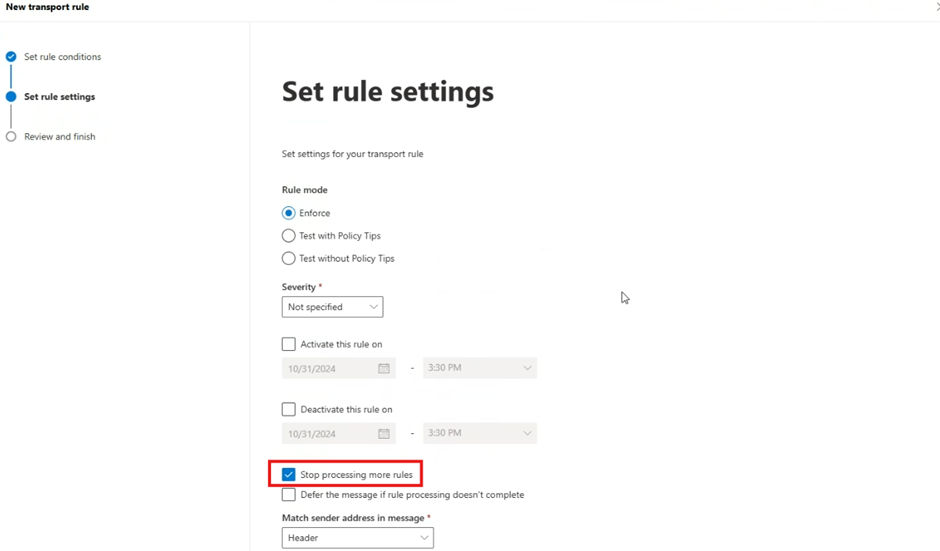
Select Next
Review the rule and click Finish