Configuring Windows Logon Protection
Below is a short guide on how to set up the Windows Login protection feature.
If you have installed the optional Windows Logon Protection component, you will normally not have to perform any further configuration.
The Windows Logon Protection component is implemented by means of a custom Credential Provider.
Windows Logon User Exclusion Groups
You may optionally configure users who should be excluded from MFA authentication during Windows Logon. To support this, two local *[1] user groups have been created on the computer during installation:
- SMS PASSCODE console exclusion: All users that are a member of this group are subject to the following rules:
- They must authenticate using MFA when they log on to the computer using a Remote Desktop (RDP).
- They will not authenticate using MFA when they log on locally using the console. I.e. only user name and Windows password are required to log on in this case.
- MS PASSCODE general exclusion: All users that are a member of this group will log on to the computer without MFA authentication – whether they log on using Remote Desktop (RDP) or locally using the console.
By default, all users being a member of the local Administrators group are automatically added during installation to the SMS PASSCODE console exclusion group. This ensures that local administrators will always be able to log on using the local console.
*[1] The groups are created as AD groups when the SMS PASSCODE Windows Logon Protection component is installed on a Domain Controller. The groups only have effect on Windows Logon on the local computer.
Remove Desktop Logon Timeout
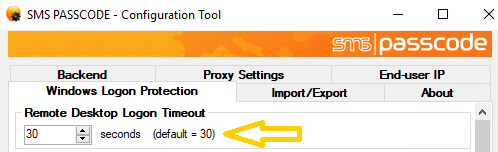
When attempting RDP access to a machine, the connection terminates within 30 seconds by default, if the Remote Desktop Logon has not completed within this time limit. This might be a problem when you are using SMS PASSCODE Windows Logon Protection, and you in some cases expect completion of SMS PASSCODE multi-factor authentications to take longer than 30 seconds; for example, in case of using advanced Dispatch Policies, where a second OTP is sent to the user, in case the first one expires. To extend the Remote Desktop Logon Timeout, select the Windows Logon Protection tab in the SMS PASSCODE Configuration tool, and select an appropriate timeout value in the top of the tab:
RDP Listener Exclusion
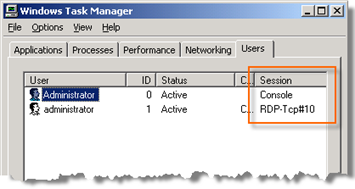
Whenever you log on to a Windows session on a Windows machine, your session is established through a specific WinStation. The most common WinStations are Console and Rdp-Tcp. The Console WinStation is used when logging on using the local console, whereas the Rdp-Tcp WinStation is used when logging on using an RDP connection (tcp port 3389 by default). The Rdp-Tcp Winstation is also called an RDP Listener.
You can see which WinStation has been used to establish each session on a machine by inspecting the Users tab in the Task Manager. Each session will be named using the name of the corresponding WinStation.
By default, when SMS PASSCODE Windows Logon Protection has been installed on a computer, all Windows sessions will be protected using SMS PASSCODE authentication, unless SMS PASSCODE authentication is skipped due to the rules of exclusion groups.
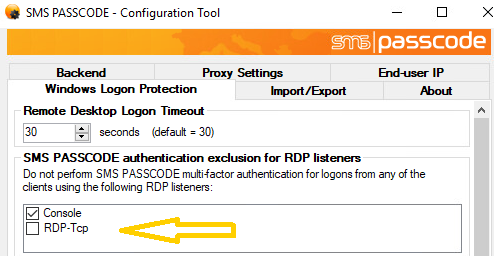
However, it is also possible to disable SMS PASSCODE Windows Logon Protection for individual WinStations. For example, you can disable Windows Logon Protection for the Console WinStation to disable SMS PASSCODE authentication for all local console logons, independent of group exclusion membership; or you can disable Windows Logon Protection for individual RDP Listeners, in case you have created some custom RDP Listeners by yourself.
WinStations / RDP Listeners exclusion is configured on the Windows Logon Protection tab of the SMS PASSCODE Configuration Tool:
Creating a Custom RDP Listener
You can create new custom RDP Listeners on a Windows machine. Why would you like to do this? For example, it might be useful in the following scenario: A machine is accessible through RDP, but you only want users to be authenticated by SMS PASSCODE Windows Logon Protection when users are logging on from the external network. When logging on from the internal LAN, users should be allowed to log on using standard Windows authentication. This can be achieved using the following setup:
- On the target machine: Create a new RDP Listener and assign a non-standard RDP port to this listener, e.g. port 4000.
- Configure your firewall to allow access on port 4000 from the external network.
- Configure your firewall to use Network-Address-Translation (NAT) regarding all RDP requests on port 4000 from the external network. NAT should be configured to transfer all RDP requests from port 3389 to port 4000. This means that all external RDP requests will connect to the target machine using the new custom RDP Listener.
- Exclude the standard RDP Listener from SMS PASSCODE Windows Logon Protection.
Using such a setup, all users on the internal LAN can make a standard RDP connection (using TCP port 3389) to the standard RDP Listener on the target machine and will be allowed to log in using standard Windows authentication, because the standard RDP Listener has been excluded from SMS PASSCODE Windows Logon Protection. All external requests will hit the target machine using the custom RDP Listener (on TCP port 4000), i.e. these users are required to perform SMS PASSCODE authentication to establish a Windows session on the target machine.
To create a custom RDP Listener, please follow this procedure:
- Make a backup of your registry.
- Open the registry using
regedit.exe. - Locate the following key: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp Right-click the key and export it to a file.
- Open the exported file. Change the name of the key
RDP-Tcpto a new name of own choice. This will be the name of the custom RDP Listener. Additionally, change any other required settings, e.g. PortNumber. Save the file. - Import the modified file into the registry. The registry will now contain a new key with the name of the custom RDP Listener. This new key is located at the key: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations
Credential Provider Filtering
As mentioned previously, the SMS PASSCODE Windows Logon Protection component is implemented by means of a custom Credential Provider. Please notice, that the SMS PASSCODE installation will automatically disable all other installed credential providers[1] by default, restricting users to log on only using SMS PASSCODE authentication.
If you wish to allow users to log on using other installed Credential Providers, you can enable these Credential providers on the Windows Logon Protection tab of the SMS PASSCODE Configuration Tool:
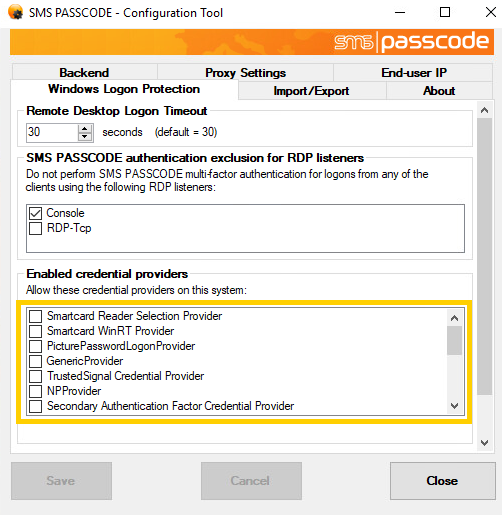
[1] Actually the SMS PASSCODE installation might leave some specific 3rd party credential providers enabled that are known to co-exist with SMS PASSCODE without disabling or conflicting with SMS PASSCODE authentication during the Windows Logon. The VMware Credential Provider installed on VMware View 4.0 clients is an example of this.
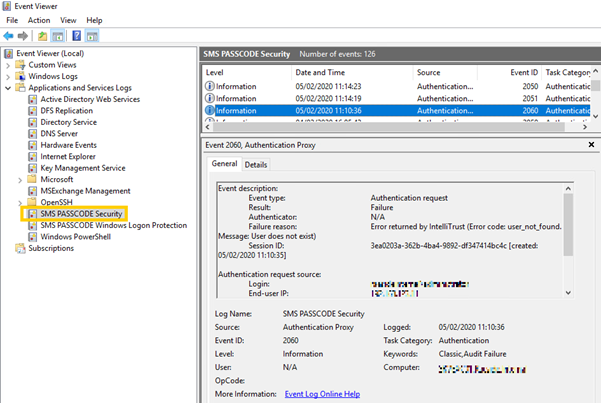
Troubleshooting
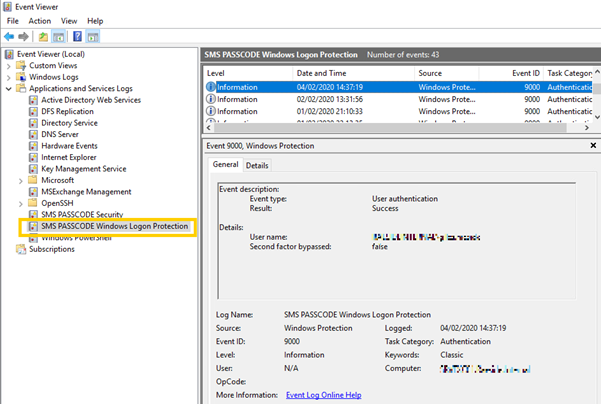
The Event log SMS PASSCODE Security shows if there has been an error with the authentication process such as the users is not enabled for Cloud MFA.
The Event log SMS PASSCODE Windows Logon Protection shows if the user's request has been bypassed with by the local SMS PASSCODE exclusion group or via the Cloud MFA rules within the USS platform.