Configuring AD FS Protection
This document is intended for Cloud MFA administrators.
The SMS PASSCODE Active Directory Federated Services (AD FS) Protection component adds multi-factor authentication to applications that are accessible via AD FS. This section describes how to configure AD FS Protection.
AD FS Protection allows you to apply multi-factor authentication to all authentication scenarios supported by the AD FS infrastructure, from access to cloud applications and internal web sites, to the provisioning of devices during workplace joins.
If you have already successfully configured your AD FS infrastructure, then you simply need to install the SMS PASSCODE AD FS Protection component on your AD FS server(s) and enable the SMS PASSCODE multi-factor authentication adapter in the AD FS management console afterwards. The procedure for this is described below.
If you have not successfully configured AD FS then you should not proceed until that has been completed.
Background
AD FS is an optional Windows Server role in Windows Server 2012 R2 / 2016 / 2019. It provides an infrastructure that allows identity validation during access to different types of services, using the AD identities of your organization. Examples of “services” are:
- Cloud applications, like Microsoft Office 365, Google Apps and SalesForce.
- Internally hosted websites published through the Microsoft Web Application Proxy. For example, you can publish an internally hosted Outlook Web Access site.
- Workplace joins, allowing people within your organization to approve devices (smartphones and tablets) to let them access data within your organization.
Any such authentication scenarios supported by the AD FS infrastructure can be extended with SMS PASSCODE multi-factor authentication (MFA), by installing SMS PASSCODE AD FS Protection on your AD FS server(s) and enabling MFA for the applications of your choice, in the AD FS management console.
AD FS Infrastructure
This section describes which servers you should install the SMS PASSCODE AD FS Protection component.
When deploying AD FS, there are two important server roles: The AD FS main server(s), responsible for performing the actual authentications, and the Web Application Proxy server(s), used for publishing HTTP/HTTPS based applications for external access, as well as functioning as AD FS Proxies. In such a configuration, you will need to install SMS PASSCODE AD FS Protection on the AD FS main server(s), not on the Web Application Proxy servers.
The installation of the AD FS Protection component on each AD FS server will install a so-called SMS PASSCODE AD FS MFA Adapter on every such server. You need to configure this MFA Adapter to activate SMS PASSCODE multi-factor authentication. This is described the below sections for AD FS 2012 R2 and 2016/2019 respectively.
Configuring the MFA Adapter for AD FS 2012 R2
This section applies to Windows Server 2012 R2. This sections describes how to enable the SMS PASSCODE MFA Adapter, after you have installed it on your AD FS server (or on every AD FS server, in case of an AD FS farm).
In order to enable the MFA Adapter, please follow the procedure below:
- Open the AD FS Management console (Microsoft.IdentityServer.msc) on your primary AD FS server:
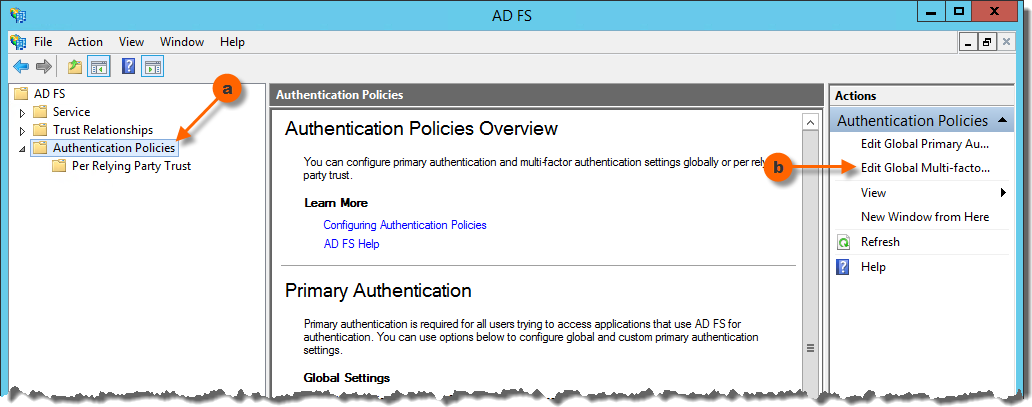
- In the AD FS Management console select the Authentication Policies node in the tree to the left.
- In the Actions pane, click Edit Global Multi-factor Authentication… and the dialog Edit Global Authentication Policy opens, with the tab Multi-factor selected.
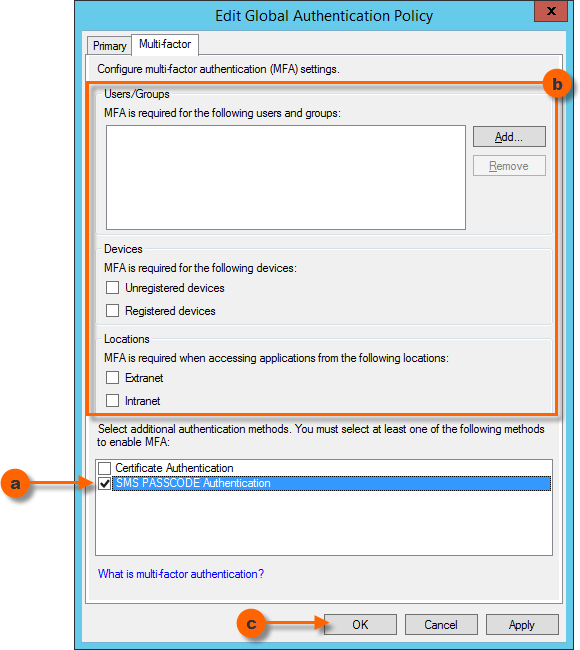
- In the bottom list box, select the checkbox SMS PASSCODE Authentication in order to enable the SMS PASSCODE MFA Adapter.
- Additionally, in order for multi-factor authentications to be triggered, you need to specify the conditions for multi-factor authentication to occur. Either you can specify conditions directly here, on the Global Authentication Policy, which will affect all applications (“Relying Parties”) – or you may leave the conditions empty here, if you prefer to set individual MFA conditions per application afterwards*. As can be seen, MFA can be activated for specific users/user groups, and/or specific devices (unregistered vs. registered), and/or requests from specific locations (extranet vs. intranet). For example, you can add the user groups here, from which you are importing SMS PASSCODE users. This will ensure, that all SMS PASSCODE users must perform multi-factor authentication. Alternatively, just select the Extranet checkbox in order to ensure, that external requests from any user are multi-factor authenticated.
- Click the OK button
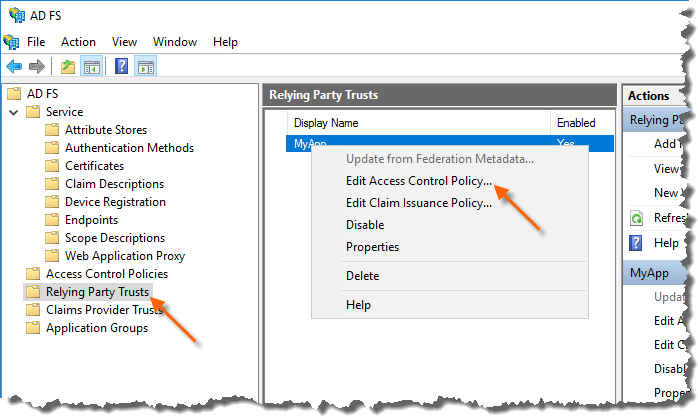
*MFA conditions can be set on a Relying Party Trust, by selecting the specific Relying Party Trust in the AD FS management console, and then click Edit Custom Multi-factor Authentication… in the Actions pane.
Configuring the MFA Adapter for AD FS 2016/2019
This section applies to Windows Server 2016 / 2019. This section describes how to enable the SMS PASSCODE MFA Adapter, after you have installed it on your AD FS server (or on every AD FS server, in case of an AD FS farm).
In order to enable the MFA Adapter, please follow the procedure below:
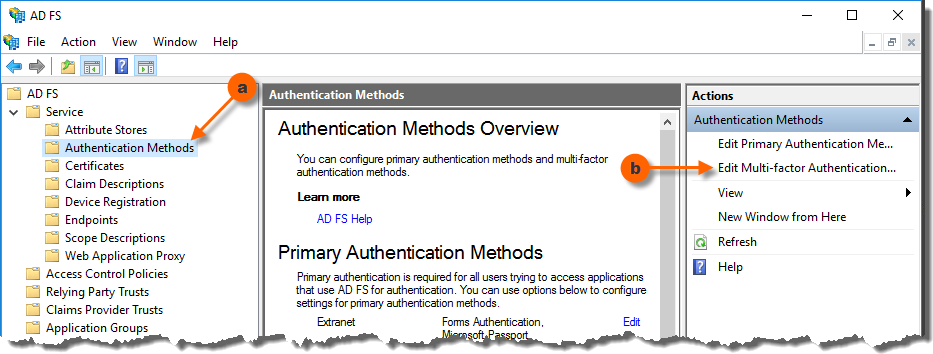
- Open the AD FS Management console (
Microsoft.IdentityServer.msc) on your primary AD FS server. - In the AD FS Management console select the Authentication Methods node in the tree to the left.
- In the Actions pane, click Edit Multi-factor Authentication Methods…
- The dialog Edit Authentication Methods opens, with the tab Multi-factor selected. In the list box, select the checkbox SMS PASSCODE Authentication to enable the SMS PASSCODE MFA Adapter, then click the OK button.
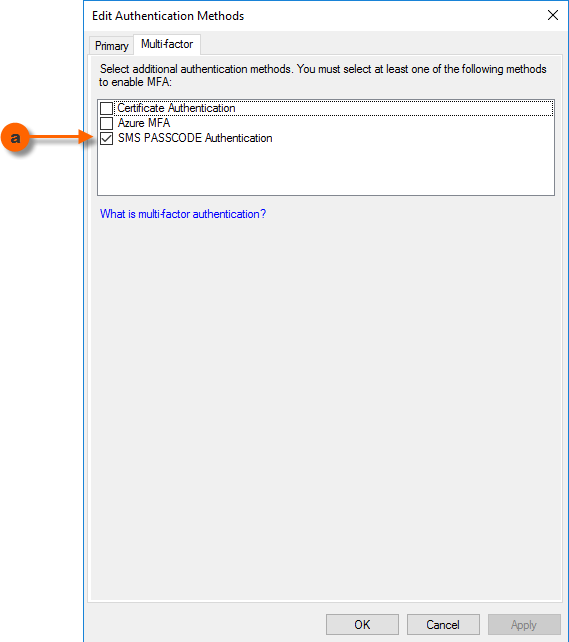
- Additionally, for multi-factor authentications to be triggered, you need to specify the conditions for multi-factor authentication (MFA) to occur. This is done by assigning an Access Control Policy that requires MFA to the Relying Party Trusts, where you want MFA to occur.