LinkScan: on-demand URL protection
- How to set up LinkScan
- LinkScan URL Rewriting
- Setting up LinkScan on USS Email Security
- Add a LinkScan Rule
- Modes of operation for LinkScan
- Auto Redirect, Block on threat, Show target URL with Doc Scan
- Auto Redirect, Block on threat, Hide target URL with Doc Scan
- Auto Redirect, Continue on threat, Hide target URL with Doc Scan
- Click to Continue, Block on threat, Show target URL with Doc Scan
- Click to Continue, Block on threat, Hide target URL and Doc Scan
- Click to Continue, Continue on threat, Show target URL, Doc Scan
- Creating exclusions
The reputation of URLs contained in an email is checked at the time of processing using the URL Scanner Rule condition. With LinkScan, further checks are conducted the moment the end-user clicks the link, including deep redirect scanning and document detection. This adds a greater degree of security, as often it can take a while for threat intelligence feeds to report that an email is a spam or has a malicious URL inside it.
Conducting further checks when the user attempts to access the URL can detect a changed URL reputation (which may not have been known at the time of delivering the email). With LinkScan, all URL links are automatically rewritten in the email, and changed to an encoded LinkScan address. The encoded address performs additional checks against multiple threat intelligence feeds dynamically, at the time of access.
There are six modes of operation available for LinkScan, each of which provides flexibility in how users interract with Linkscan-rewritten URLs.
How to set up LinkScan
LinkScan URL Rewriting
LinkScan rewrites URLs so that they will always pass through the linkscan.io domain before being silently redirected. A LinkScan URL has the format:
https://linkscan.io/scan/ux/<string>
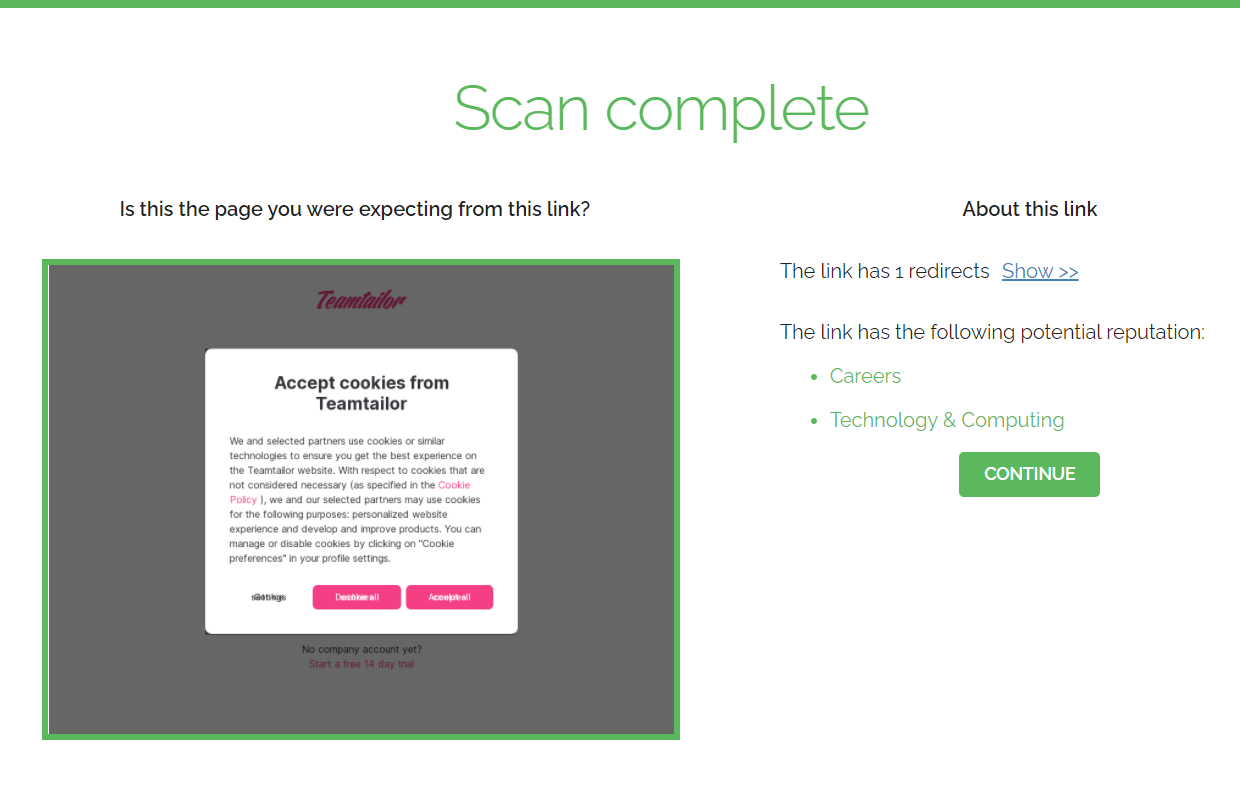
When a user clicks a LinkScan-rewritten URL, the LinkScan service begins checking the underlying URL against multiple threat intelligence feeds. The following example shows a clean URL with the Click to Continue operating mode enabled:
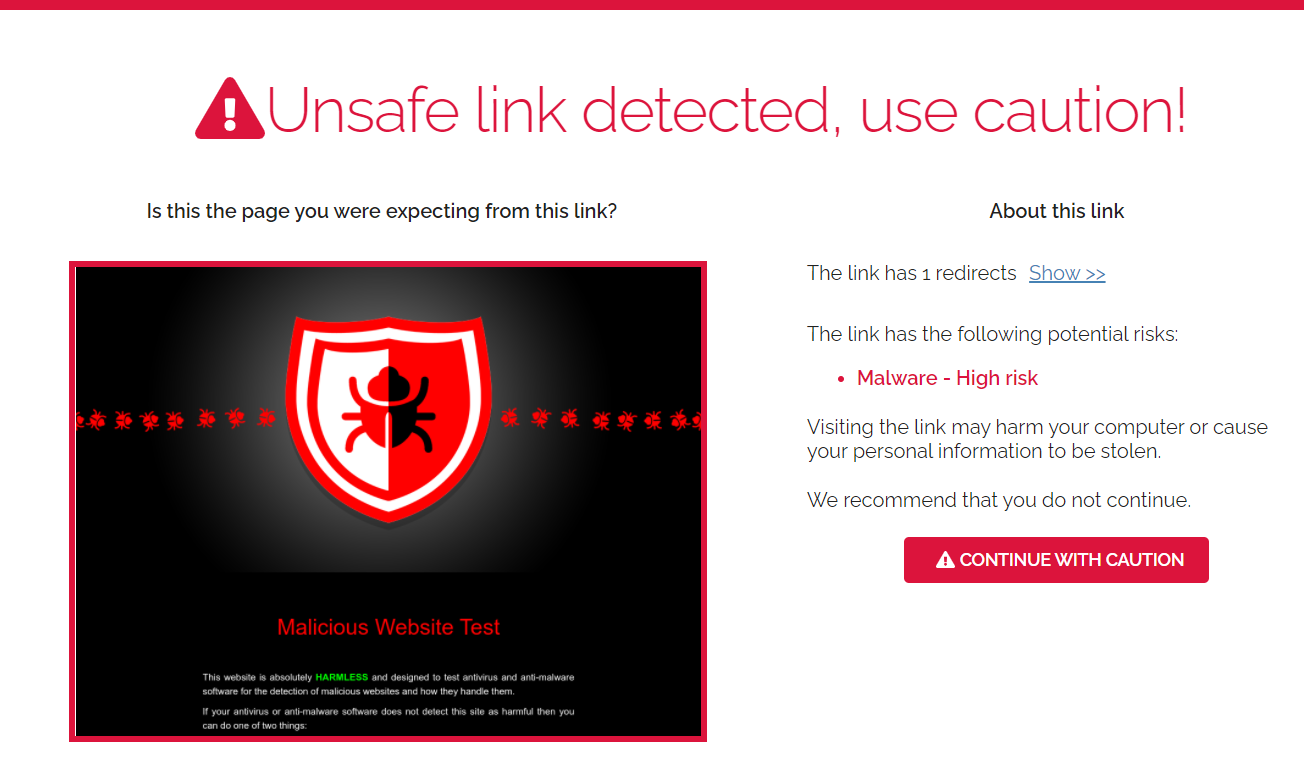
The following example shows a URL that has a threat with the Auto Redirect unless Threat Detected operating mode enabled:
Converting a rewritten URL back to its original URL
You can use the online tool at https://linkscan.io/reveal to reveal the original URL from a LinkScan-rewritten URL.
Setting up LinkScan on USS Email Security
Add a LinkScan Rule
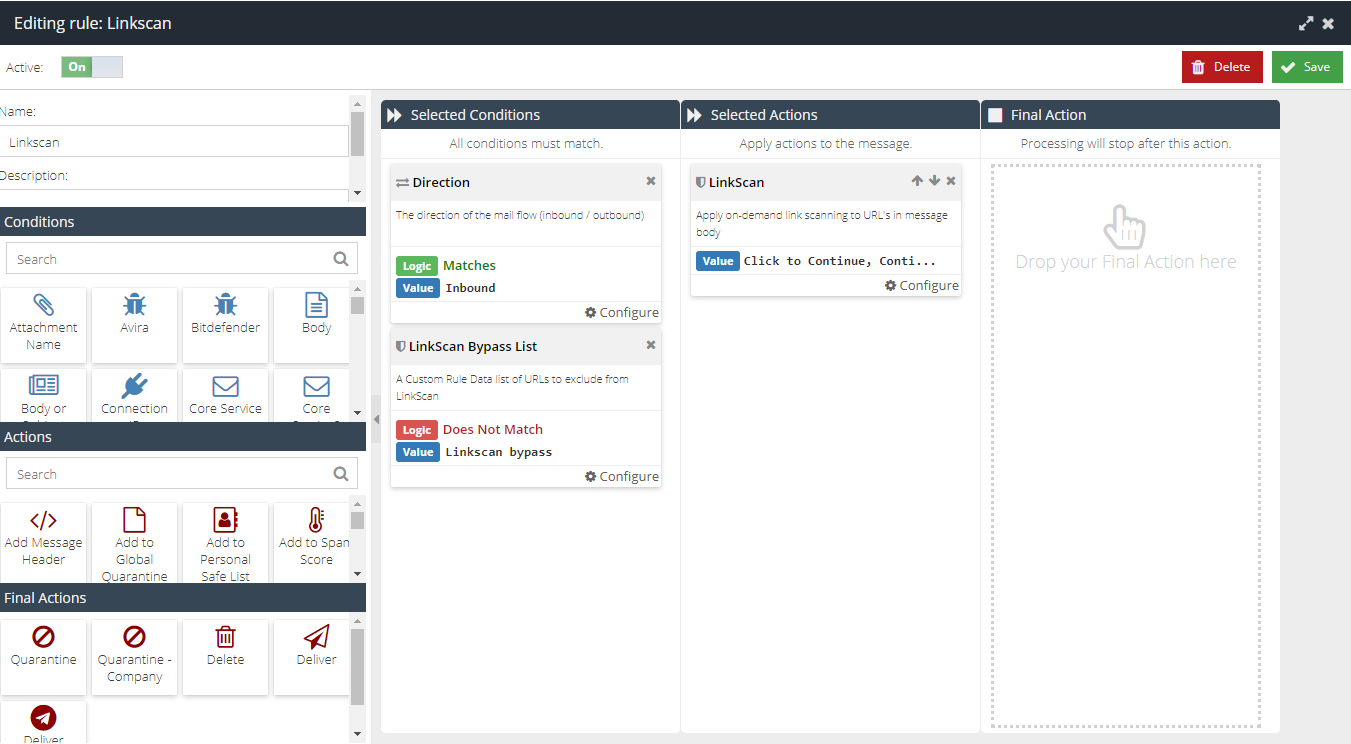
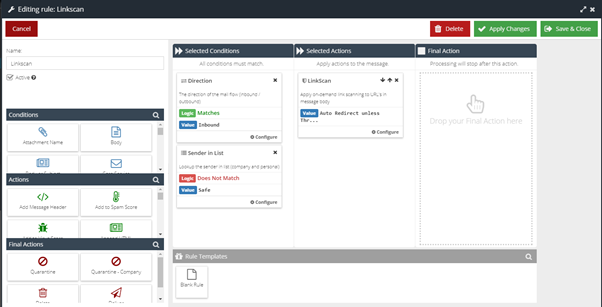
If you do not already have a LinkScan Rule, you can create it using these steps.
- Visit your USS Dashboard and click Products ⟶ E-mail Security ⟶ Message Rules.
- Click
 to create a new Rule.
to create a new Rule. - Give your new Rule a sensible name, like LinkScan.
- Add a Direction Condition, with the direction set to Match Inbound.
- Add a Sender In List Condition, with the logic set to "Does Not Match: Safe".
- Add a LinkScan Action. Set the Value to Auto Redirect unless Threat Detected.
- Do not add a Final Action.
- Click
 .
.
Modes of operation for LinkScan
LinkScan can operate in a number of different operating modes. The specific mode is chosen in the LinkScan Message Rule.
Auto Redirect, Block on threat, Show target URL with Doc Scan
The user is automatically redirected to the target URL unless a threat is detected. If the target is an embedded document (e.g. Onedrive, PDF, Dropbox) then the document will also be scanned for URLs that may be a threat. If a threat is detected, there is no option to continue to the target URL. The target URL is visible on the linkscan.io scan page.
Auto Redirect, Block on threat, Hide target URL with Doc Scan
The user is automatically redirected to the target URL unless a threat is detected. If a threat is detected, the reason will be displayed with no option to continue and the destination URL will be hidden. If the target is an embedded document (e.g. Onedrive, PDF, Dropbox) then the document will also be scanned for URLs that may be a threat.
Auto Redirect, Continue on threat, Hide target URL with Doc Scan
The user is automatically redirected to the target URL unless a threat is detected. If a threat is detected, the reason will be displayed with a continue button available and the destination URL will be hidden. If the target is an embedded document (e.g. Onedrive, PDF, Dropbox) then the document will also be scanned for URLs that may be a threat.
Click to Continue, Block on threat, Show target URL with Doc Scan
Requires a click to continue if the URL is checked and passes all checks. If a threat is detected, there is no option to the target URL. The target URL is visible on the linkscan.io scan page. If the target is an embedded document (e.g. Onedrive, PDF, Dropbox) then the document will also be scanned for URLs that may be a threat.
Click to Continue, Block on threat, Hide target URL and Doc Scan
Requires a click to continue if the URL is checked and passes all checks. If a threat is detected, there is no option to the target URL. The target URL is not visible on the linkscan.io scan page. If the target is an embedded document (e.g. Onedrive, PDF, Dropbox) then the document will also be scanned for URLs that may be a threat.
Click to Continue, Continue on threat, Show target URL, Doc Scan
Requires a click to continue if the URL is checked and passes all checks. If a threat is detected, a button is shown to allow to continue to target URL. The target URL is visible on the linkscan.io scan page. If the target is an embedded document (e.g. Onedrive, PDF, Dropbox) then the document will also be scanned for URLs that may be a threat.
Creating exclusions
You can exclude specific sender addresses, specific URLs, or parts of URLs, from LinkScan's engine.
Excluding specific sender addresses
Add the sender address to the Safe List. LinkScan will not rewrite URLs in any emails from this sender.
Excluding URLs
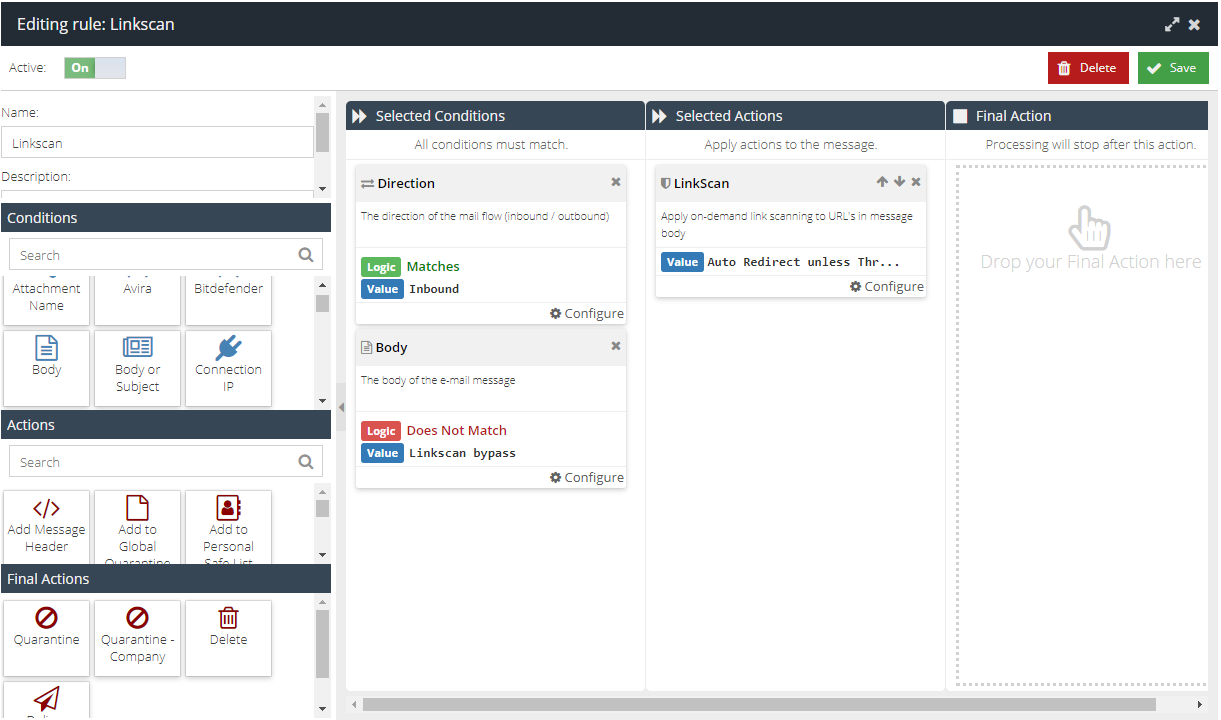
Create an exclusion for the URL by create a new set of Custom Rule Data.
- Visit your USS Dashboard and click Products ⟶ E-mail Security ⟶ Custom Rule Data.
- Click
 to create new RegEx Custom Rule Data.
to create new RegEx Custom Rule Data. - Give your new data a sensible name.
- In the Value field, add the URL you want to exclude from LinkScan processing.
apple.com would become \b(apple\.com)\b. Make sure that you escape any period characters (.) in the URL with a slash (\).(?i)\b(apple\.com)\b|\b(www\.microsoft\.com)\bThis will match on Apple.com and apple.com as well as www.Microsoft.com
apple.com and www.microsoft.com would be \b(apple\.com)\b|\b(www\.microsoft\.com)\b.- Click Save to save this new Custom Rule Data.
- Navigate to Products ⟶ E-mail Security ⟶ Message Rules. Double-click the LinkScan Rule to open it for editing.
- Add a new Body or LinkScan Bypass List Condition. Set the Logic to Does Not Match and the Value to the new Custom Rule Data you created.