Connection Rules
Unlike Message Rules (which are executed against individual emails), Connection Rules are applied to every attempt to connect to or from your mailboxes. You can use Connection Rules to preemptively reject emails that fit certain criteria (such as emails with a particularly large size, or emails from an IP address with a poor reputation).
Managing Connection Rules
To see the Connection Rules currently in place for your Email Security account, visit your USS Dashboard and click Security Modules ⟶ Email Security ⟶ Connection Rules.
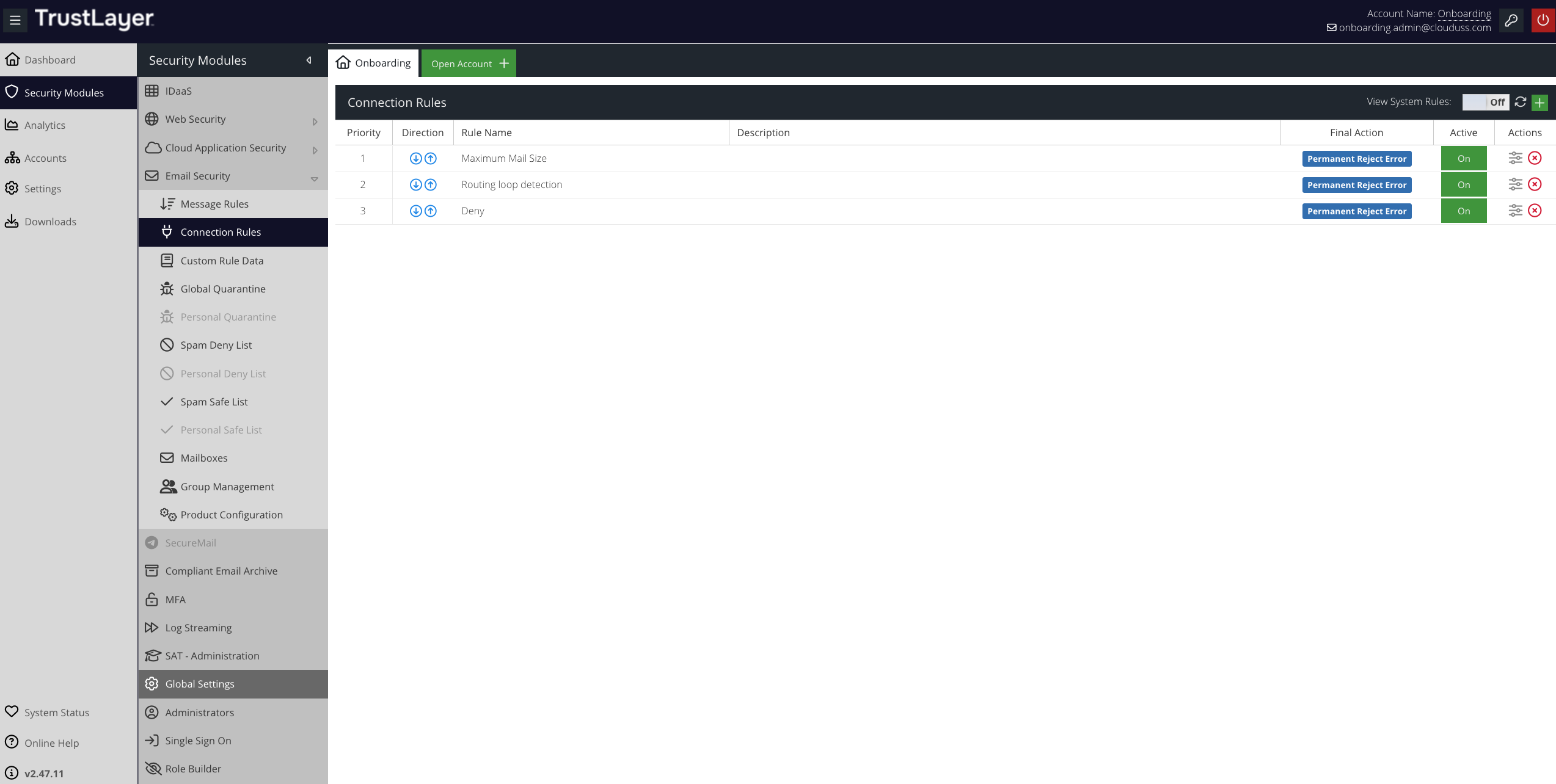
Rules priority
Connection Rules are processed in order as they appear on the Connection Rules screen. So, the Rule at the top of the list (with the Priority of 1) will be executed first.
Direction
A Rule may be processed only against incoming connections, only against outgoing connections, or against both. The Direction column indicates when the Rule will be processed.
 | This Rule will only be processed against incoming connections. |
 | This Rule will only be processed against outgoing connections. |
 | This Rule will be processed against all connections. |
Re-ordering connection rules
To change the order in which your Connection Rules are processed, simply left-click a Rule in the list, and drag it to a new position.
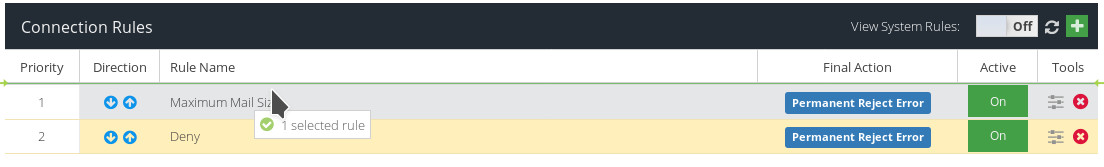
Deleting a connection rule
To delete a Rule, click the  icon next to the Rule you want to delete.
icon next to the Rule you want to delete.
You can also delete a Rule within the Rule Builder window by clicking  .
.
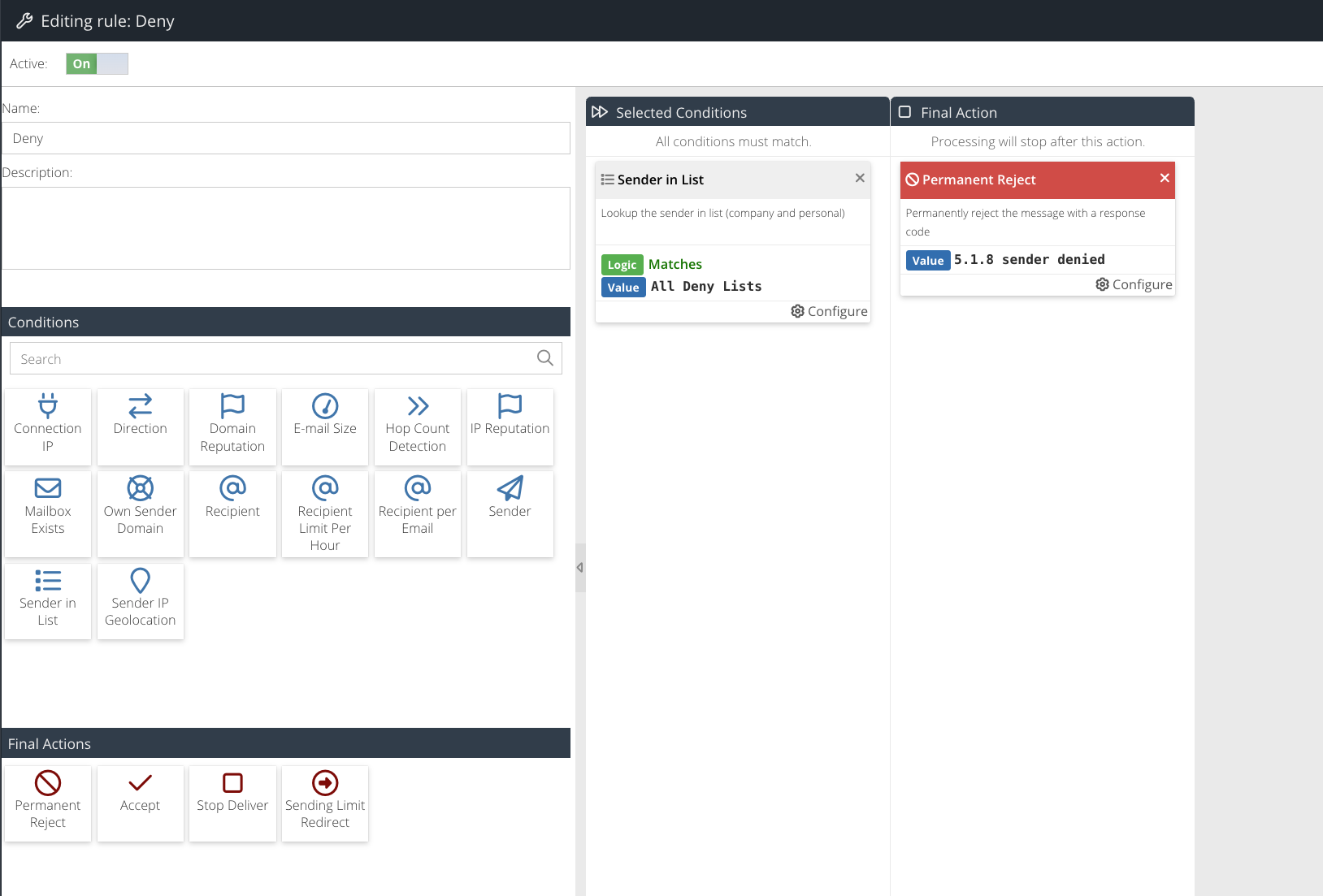
Editing a connection rule
To edit a Rule, double-click it in the list. The Rule Builder will open.
Make any changes you wish, and then click  .
.
Inactive rules
A Rule can be set to be inactive. An inactive Rule will never be triggered. You can easily see which Rules are inactive in the Connection Rules window, where the Active column will list each rule as being either  or
or  .
.
To change the active status of a Rule, double-click the Rule to edit it, and then check or uncheck the Active checkbox.

Creating a new Rule
To create a new Connection Rule, click the  icon. Give your new Rule a sensible name, and click
icon. Give your new Rule a sensible name, and click  .
.
The Rule Builder Window will be displayed.
Name
If you want to rename your new Rule, enter a new name here.
Active
Newly created Rules are inactive by default. To set your new Rule as active, enable the checkbox.
Conditions
You can apply one or more Conditions to your Rule. Each condition limits the circumstances under which this Rule will match.
Connection IP
Check if the email's IP address (either the sender's IP or the destination IP) matches a particular pattern. You can choose to match against localhost addresses, or select from any Custom Rule Data you've created.
Direction
Choose whether this Rule should be run against inbound email (mail coming in to addresses on your server) or outbound email (mail sent by users on your server).
E-mail Size
The Condition will match if the email's total size matches the specified Condition Value. For example, if the email size is less than 4kb, or if the email size is greater than 20mb.
IP Reputation
Use this Condition to check if the IP address of the email's originating server matches a specified reputation value.
Mailbox Exists
Check whether the mailbox to which the email is addressed exists on your server.
Recipient
This Condition can be used to test against the email's recipient. You can check whether the recipient appears in your Active Directory export, or you can test against any Custom Rule Data you have created.
Sender
Use this Condition to check whether the sender of the email matches a specific pattern.
Sender in List
Use this Condition to check whether the sender is in the Safe or Deny lists.
Sender IP Geolocation
Use this Condition to check whether the sender's purported IP originates from a specific country or countries.
Final Actions
Use Final Actions to determine what will ultimately happen to a connection that triggers your Rule.
You can only add one Final Action to a Rule.
Permanent Reject
Use this Final Action to permanently reject this connection. You can choose from a list of standard response codes with which to reject the message.
Accept
Accept this connection. This will allow the message to then be processed by your Message Rules.
System rules
Your Email Security installation comes with a number of out-of-the-box System Rules, provided by your Service Provider. These System Rules are intended to give a good set of initial base rules, that will protect a typical email system from most threats. System Rules cannot be changed or disabled, although you can of course override them with your own Rules.
System Rules are not shown in the Connection Rules window by default. To display them, click the  toggle.
toggle.
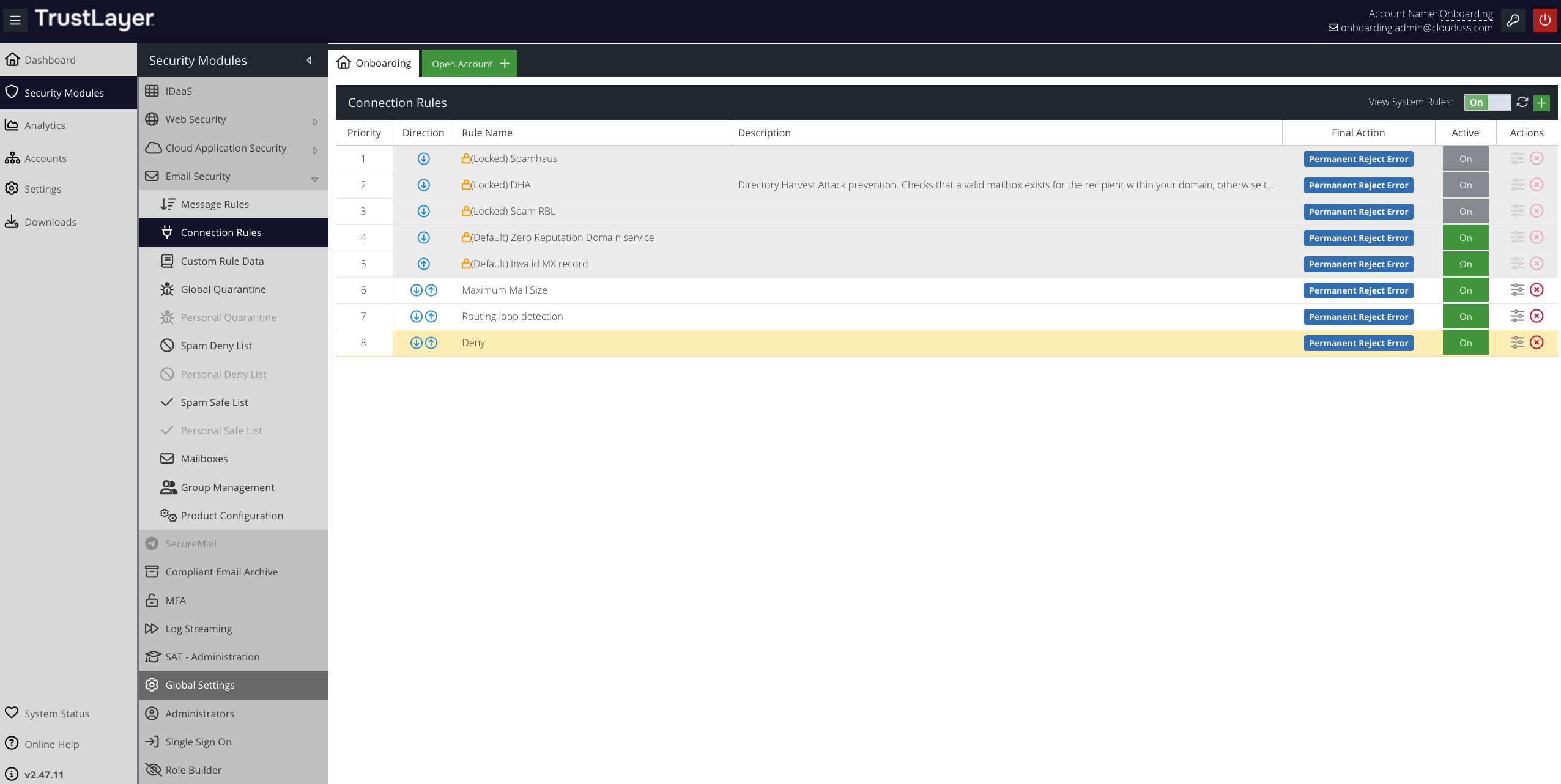
You can double-click a System Rule to view details of exactly what Conditions and Final Actions it consists of.