Authentication & Identification
Active Directory
USS Gateway supports Active Directory authentication, if required. USS Gateway can be configured to join multiple Active Directory domains and perform kerberos authentication (transparent) for domain based devices.
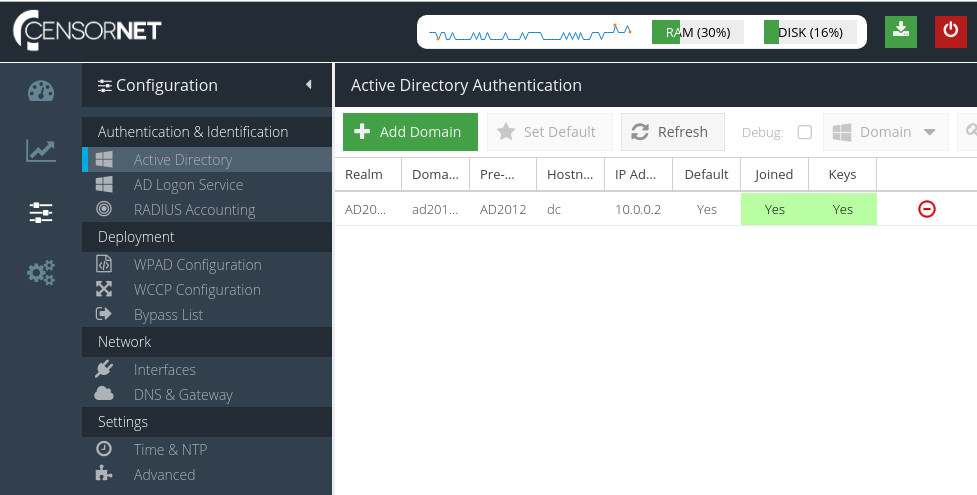
Adding a domain to Domain List
To add a domain to the list of available domains, click the  button.
button.
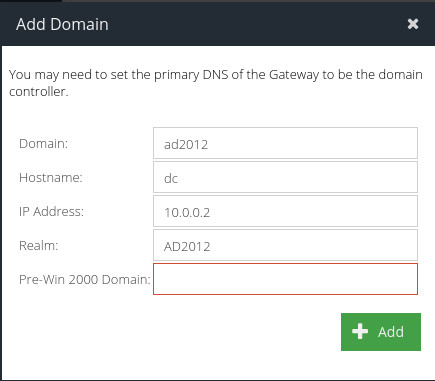
Domain
The fully qualified Active Directory domain name without the hostname.
Hostname
The hostname of the domain controller server excluding the domain name.
IP address
The IP address of the domain controller server.
Realm
This is automatically created from the domain name but can be changed if required.
Pre-Win 2000 Domain
This is automatically created from the domain name, but can be changed if required.
Click  to add the domain to the Domain List.
to add the domain to the Domain List.
You may now add additional domains to the Domain List or proceed to joining USS Gateway to the domain.
Removing a domain from the Domain List
To remove a domain from the domain list:
- Ensure the domain is no longer joined by using the Leave Domain option (see Leaving a domain, below).
- Click
 next to the domain you wish to remove.
next to the domain you wish to remove.
Joining a domain
Select one of the domains from the Domain List. Click the  drop-down menu, and Select Join.
drop-down menu, and Select Join.
You will be prompted to enter the credentials of an Active Directory user that has permission to join USS Gateway to the domain. Usually this is a Domain Admin, such as administrator.
Click OK to initiate the join to the domain. It may take up to 30 seconds for the USS Gateway to join the domain. The response will be added to the response window:
Click Close to return to the Domain List and check the status of the domain.
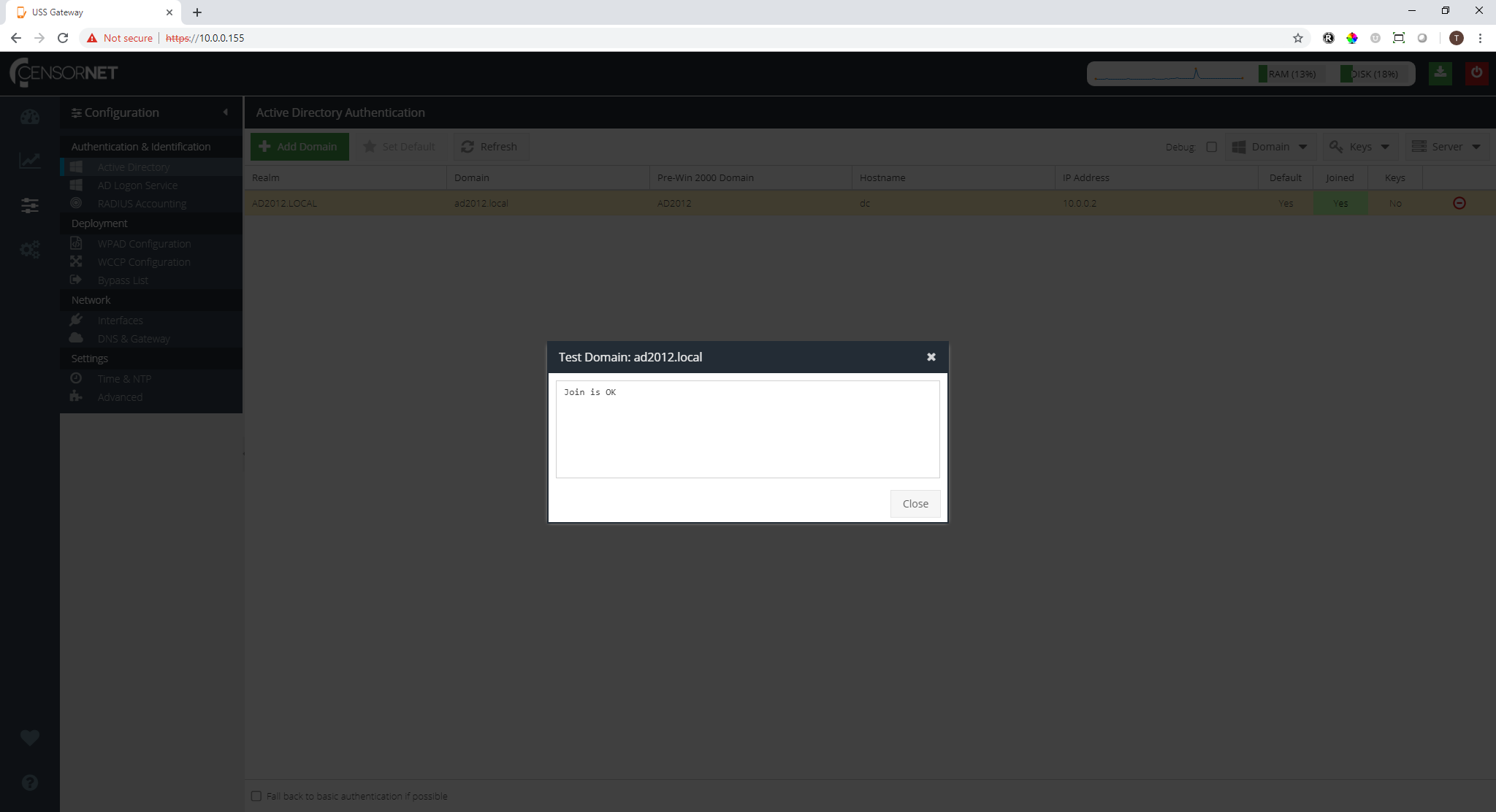
The Joined status will show Yes if USS Gateway was successfully joined to the domain. You can verify this by testing the domain. To do this, select the domain from the Domain List, click the  drop-down menu and click Test. If the join is successful, you will see a response like this:
drop-down menu and click Test. If the join is successful, you will see a response like this:
To complete the configuration, you should now create encryption keys for the kerberos protocol to use.
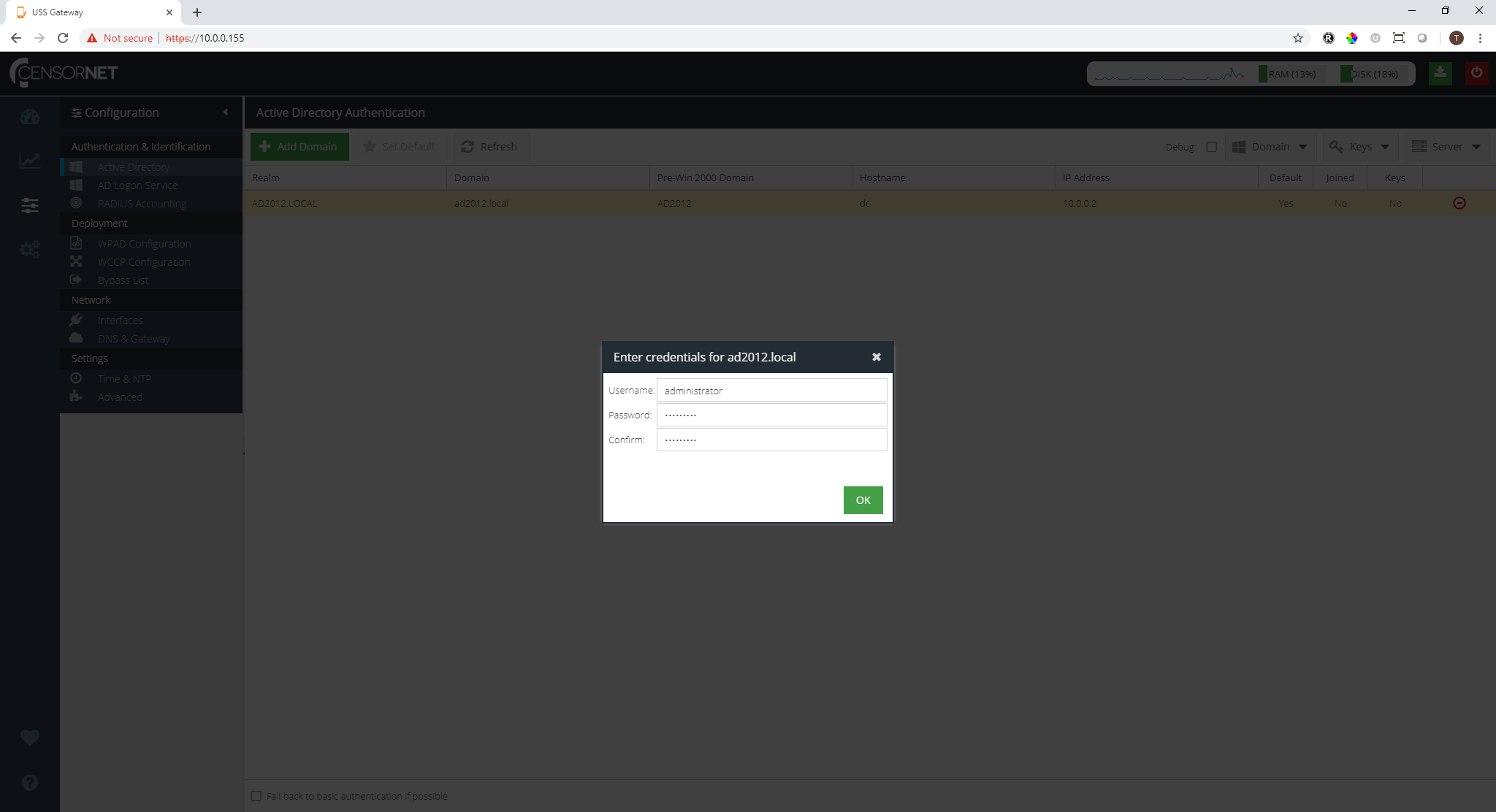
Select the domain from the Domain List and click the  drop-down menu, and select Create. You will be prompted to enter the credentials of an Active Directory user that has sufficient rights to create the keys - this is normally the administrator or a Domain Admin user.
drop-down menu, and select Create. You will be prompted to enter the credentials of an Active Directory user that has sufficient rights to create the keys - this is normally the administrator or a Domain Admin user.
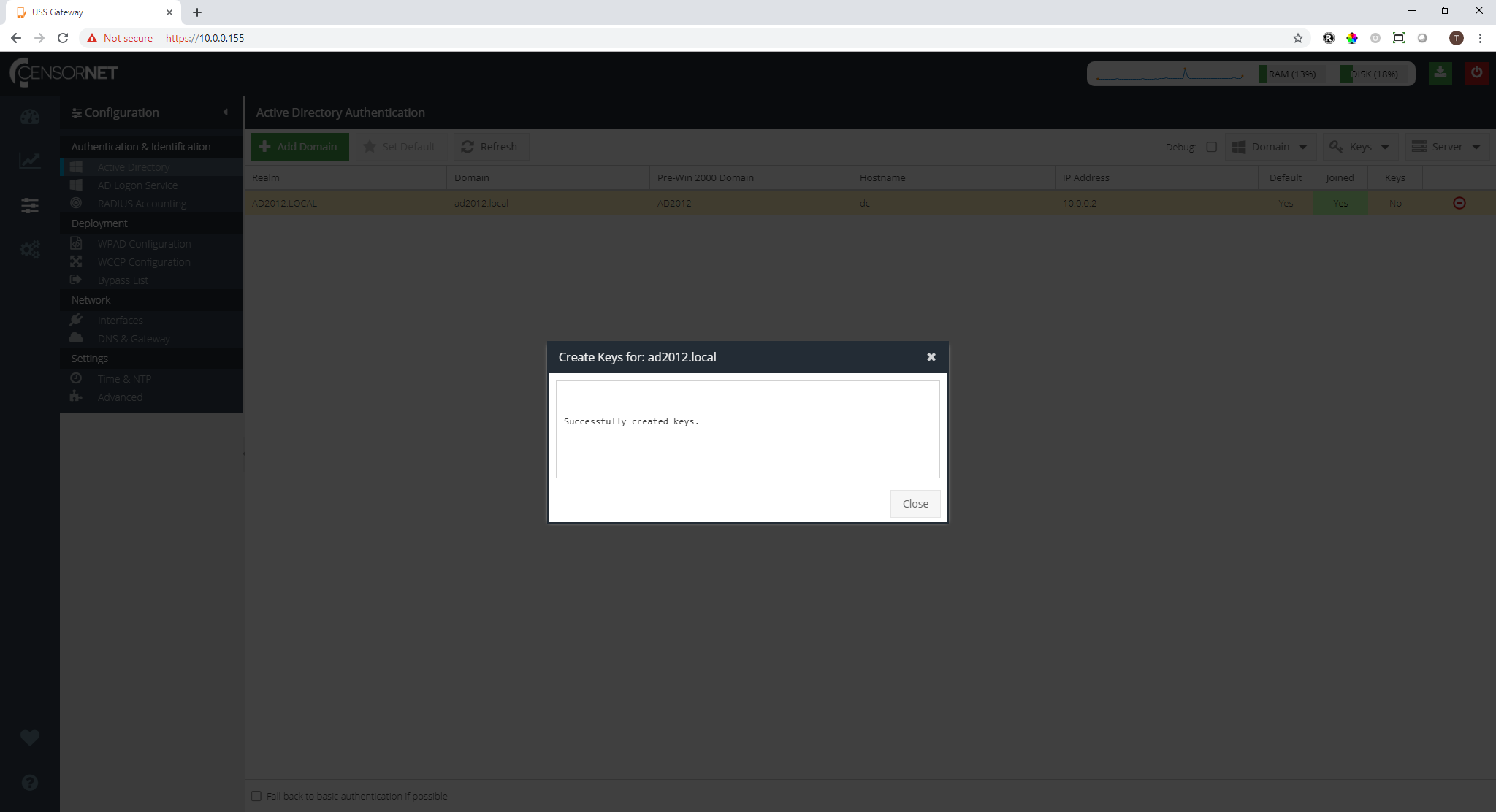
After a few moments the keys will be created:
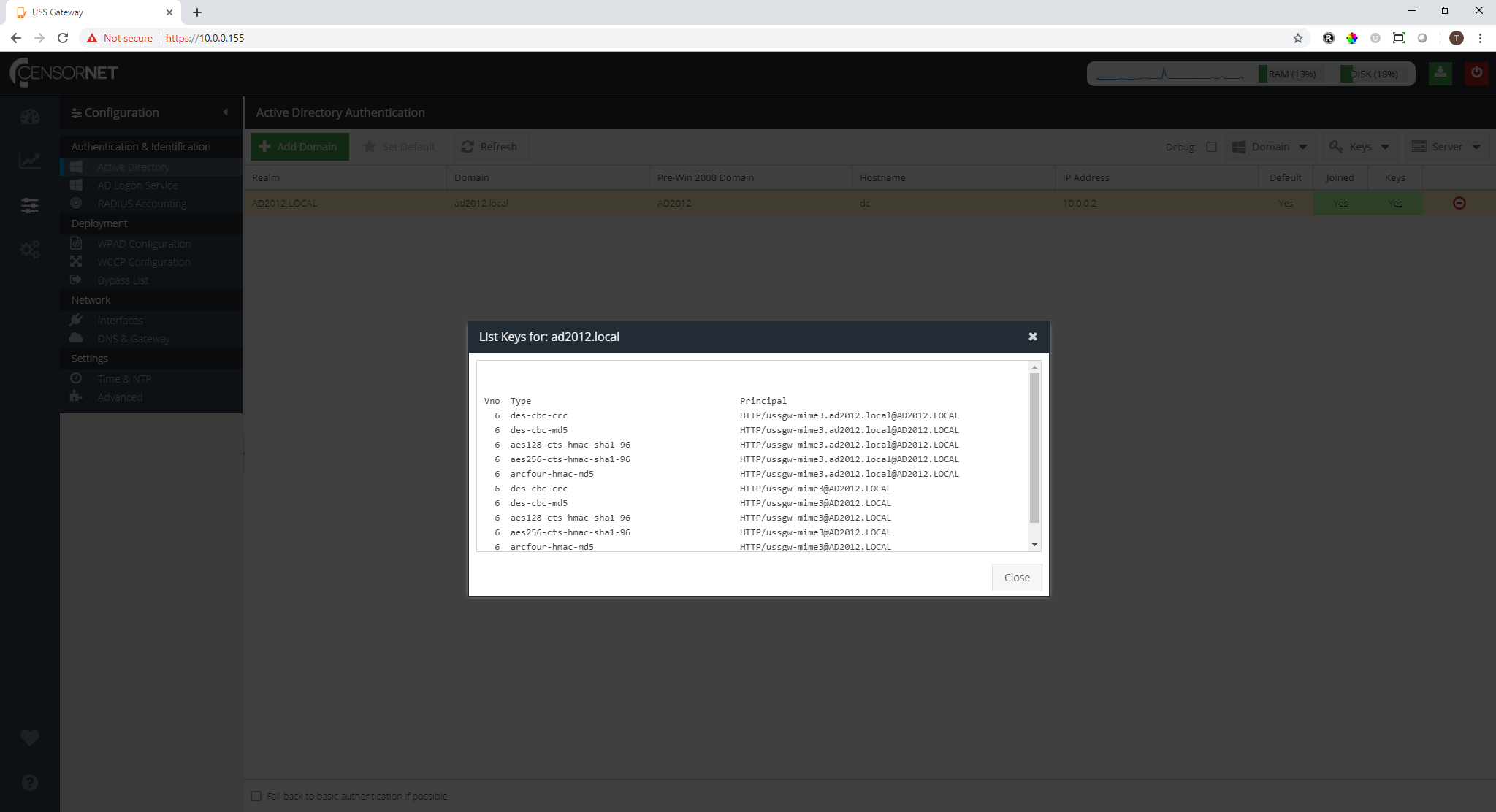
To verify that the keys have been created successfully, click the  drop-down menu and select List. The kerberos keys should be listed.
drop-down menu and select List. The kerberos keys should be listed.
The USS Gateway is fully joined to the domain if both Joined and Keys status is green:
Creating a DNS entry for USS Gateway
In order for kerberos authentication to work correctly, you must reference the USS Gateway proxy by its fully qualified domain name (FQDN) and not its IP address when configuring explicit web browser proxy settings. For this to work, you must create an A record in your DNS server for the FQDN and point it to the IP address of the USS Gateway server.
ussgw with a server IP of 10.0.0.200 and it is joined to the domain ad2012.local, the FQDN would be ussgw.ad2012.local and it should map to the IP 10.0.0.200.On Windows Server, this can be configured in DNS Manager. Click Start ⟶ Administrative Tools ⟶ DNS Manager. Right-click on the Forward Lookup Zone for your domain and click New Host (A or AAAA record).
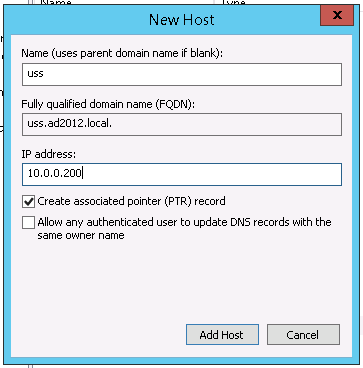
Click Add Host.
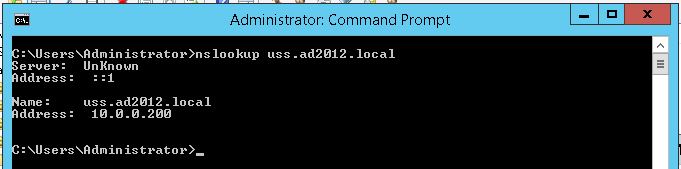
Once added, you can verify the DNS entry is working by opening a Command Prompt and attempting to resolve the FQDN e.g. nslookup uss.ad2012.local. It should resolve to the correct IP address (10.0.0.200 in the example below).
The next step is to configure web browsers to use the USS Gateway as an explicit web proxy.
Configuring Web browsers
There are several ways to configure web browsers to use the USS Gateway proxy server:
- Manually configure browser proxy settings
- Group Policy proxy configuration
- Web Proxy Auto Discovery (WPAD) script
Leaving a domain
To leave a domain, first select the domain from the Domain List.
Click the  drop-down menu, and then select Flush to remove any existing keys. You will be prompted to enter the credentials of a valid Active Directory user with permission to remove the keys.
drop-down menu, and then select Flush to remove any existing keys. You will be prompted to enter the credentials of a valid Active Directory user with permission to remove the keys.
Click the  drop-down menu and select Leave. You will be prompted to enter the credentials of a valid Active Directory user with permission to leave the domain. Verify the leave is successful by checking if the USS Gateway machine account has been removed from the Computers container.
drop-down menu and select Leave. You will be prompted to enter the credentials of a valid Active Directory user with permission to leave the domain. Verify the leave is successful by checking if the USS Gateway machine account has been removed from the Computers container.
If the leave process fails, it is possible to force the join to be broken. Click  drop-down menu, and then Force Leave. This will break the connection. However, you may have to manually remove the machine account from the Computers container on the Active Directory domain.
drop-down menu, and then Force Leave. This will break the connection. However, you may have to manually remove the machine account from the Computers container on the Active Directory domain.
Authentication Fallback
Kerberos authentication is designed for devices that are members of the Active Directory domain. In some cases, you may have devices that are not part of the domain but you would still like to authenticate them with an Active Directory username.
USS Gateway has the option to fall back to "basic" authentication if kerberos fails (due to non-domain membership). This will cause the browser to prompt the user for Active Directory credentials. To enable this option use the checkbox at the bottom of the Domain List:
AD Logon Service
You can generate a new API Key for the AD Login Service if you intend to identify users based on login events.
You can also use a key generated on another USS Gateway server. Click Use Existing Key and paste the existing key into the text field.
RADIUS Accounting Clients
A RADIUS Client is a server that will send accounting data to the USS Gateway for authenticating Captive/Guest users. If you have a RADIUS Client you wish to add, you can do so by clicking to  icon and entering a
icon and entering a Friendly Name, IP address and secret.