Configuring TLS encryption
You can use TLS to encrypt the tunnel between sending and receiving SMTP servers. This increases the security of your emails, and makes interception less likely.
Email Security provides two options for TLS encryption in Message Rules:
- Enforced TLS will cause the server to only send an email if TLS is supported by the remote site.
- Opportunistic TLS will cause Email Security to attempt a TLS connection if TLS is advertised by the remote site. If this fails, Email Security will fall back to a non-TLS connection (and plain-text SMTP).
Email Security provides Opportunistic TLS as part of the default System Message Rules. If you're an older customer, your system rules may not include this - in which case you can follow the instructions below to manually create a TLS rule.
Configuring Enforced TLS
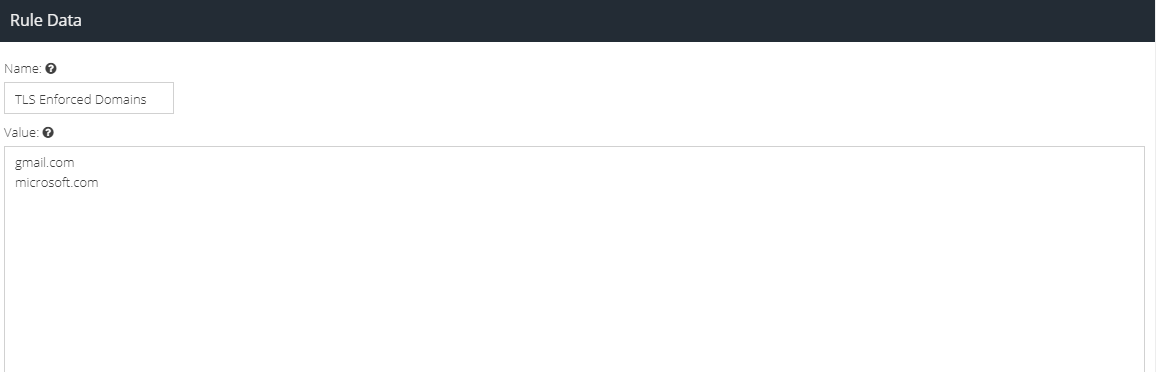
- Create a new set of Custom Rule Data covering the domains on which you want to enforce TLS. Separate each domain with a new line.
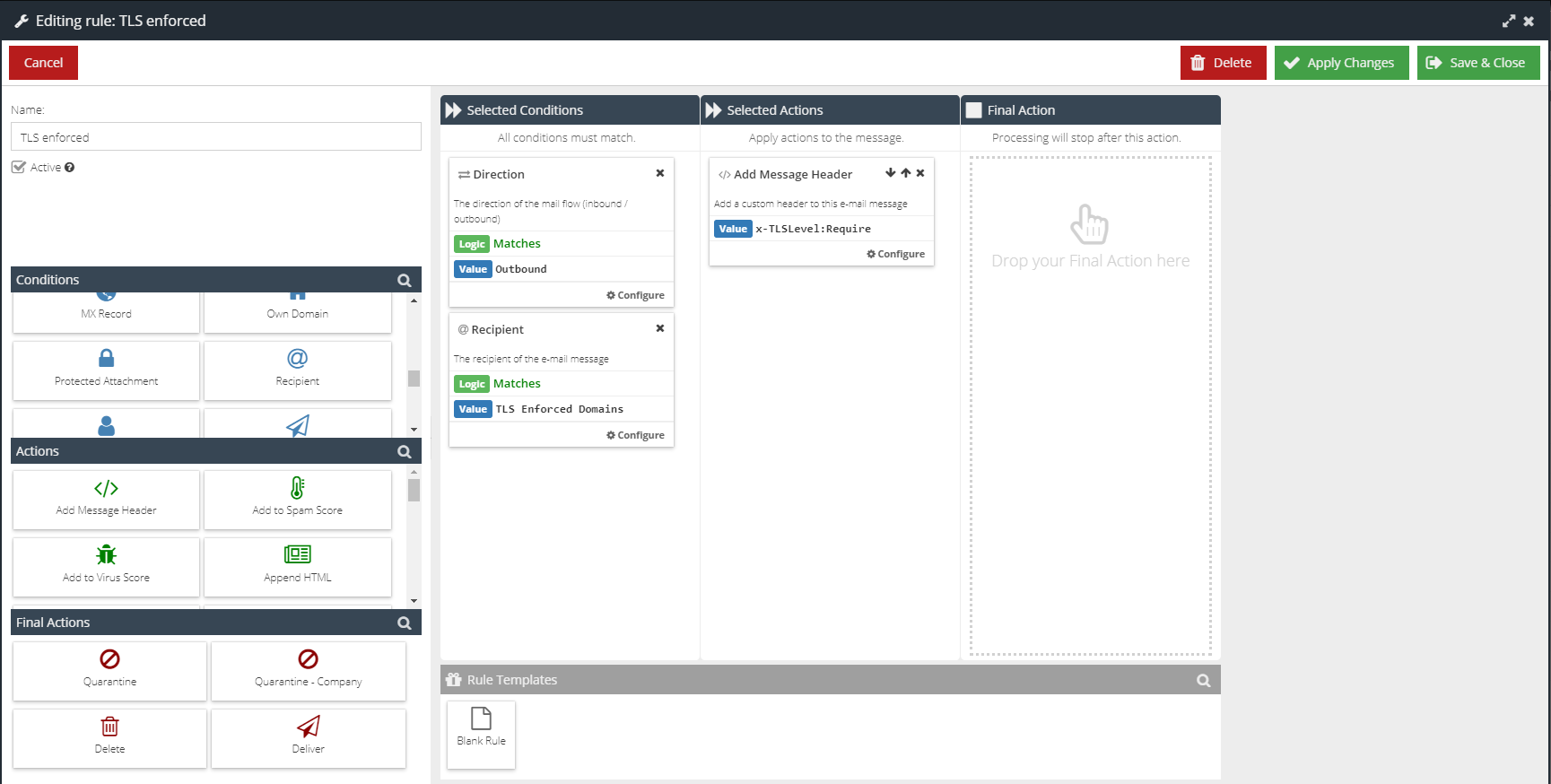
- Create a new Message Rule to add a new email header, which will force TLS delivery.
Use the following parameters for the new Rule:
Conditions | Actions | Final Actions |
Direction: Matches Recipient: Matches | Add Message Header: Value | None |
- Drag and drop this Rule above the Deliver Outbound rule.
Configure Opportunistic TLS
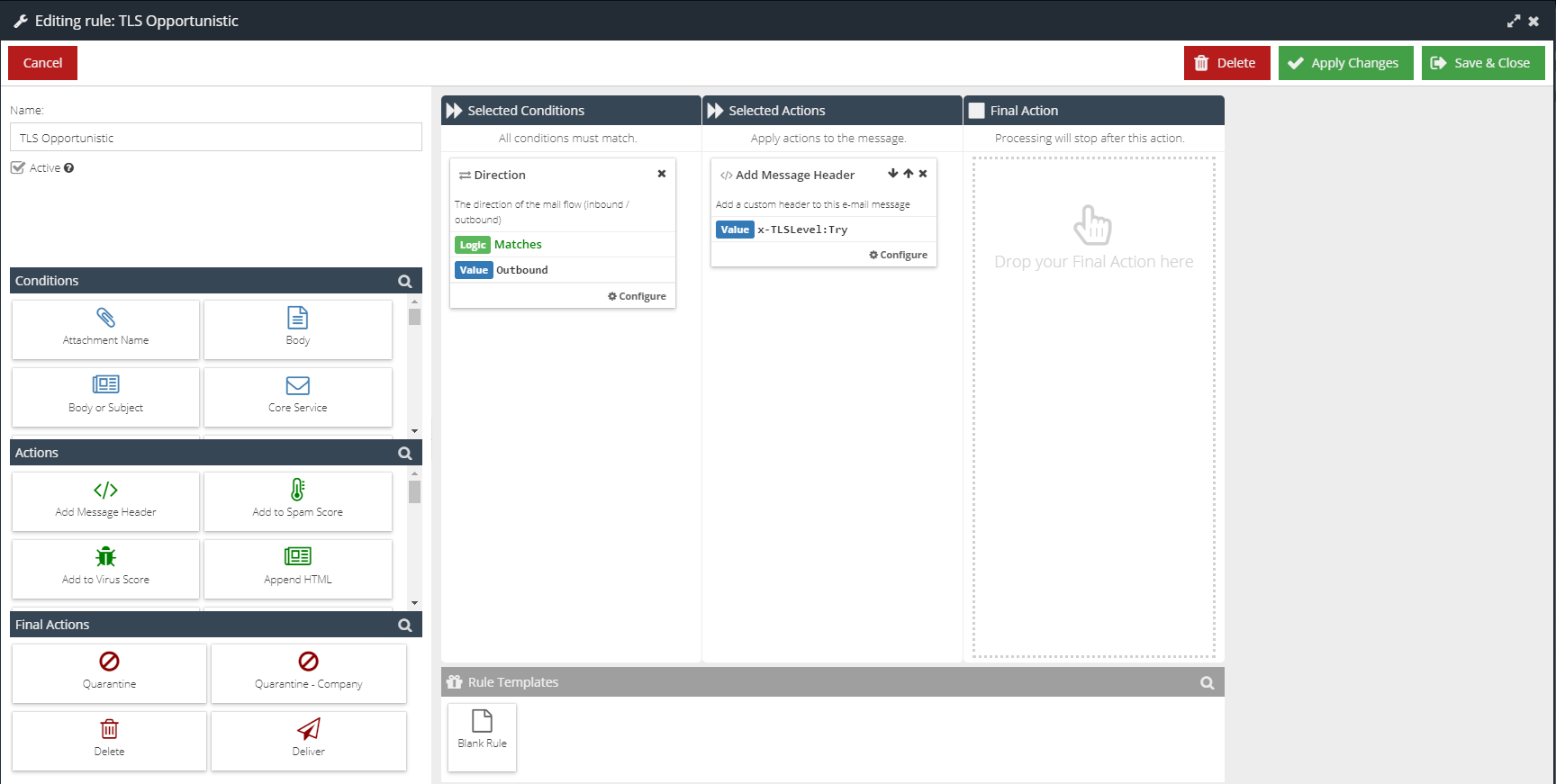
- Create a new Message Rule to add a new email header, which will force opportunistic TLS delivery.
Use the following parameters for the new Rule:
Conditions | Actions | Final Actions |
Direction: Matches | Add Message Header: Value | None |
- Drag and drop this Rule above the Deliver Outbound rule.
Using Enforced TLS and Opportunistic TLS together
- If you want to use both Enforced and Opportunistic TLS at the same time, follow the steps above to set up Enforced TLS and Opportunistic TLS.
- Add an additional Condition to your Message Rule for Opportunistic TLS:
Conditions | Actions | Final Actions |
Direction: Matches | Add Message Header: Value | None |
Recipient: Does Not Match |
The delivery engine will look for the first x-TLSLevel header entry, and will use that to process the email. Adding this additional Rule Condition avoids emails ending up with two x-TLSLevel headers (which could give unexpected results).