Settings
Time & NTP
To configure time settings for your USS Gateway, click Configure ⟶ Settings ⟶ Time & NTP.
The Time & NTP section allows you to set the local time of the USS Gateway server. This is important, especially if you intend to use Active Directory authentication.
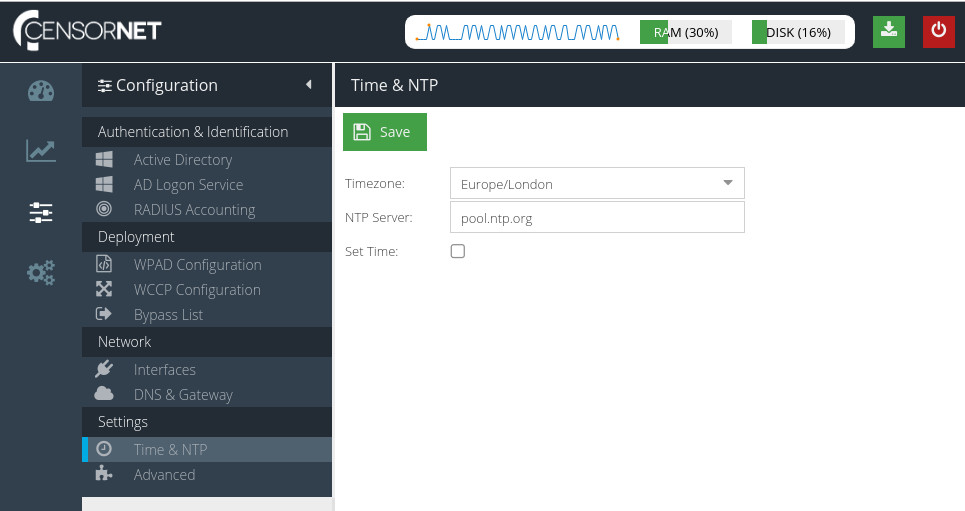
Timezone
The timezone that best describes the location of the USS Gateway server.
NTP server
To ensure the server clock is always up to date, we recommend you use NTP (Network Time Protocol). Enter your preferred NTP server here (hostname or IP address).
pool.ntp.org.Set Time
If you wish to set the server time manually, check this option and enter the correct time.
Advanced
To configure advanced settings for your USS Gateway, click Configure ⟶ Settings ⟶ Advanced.
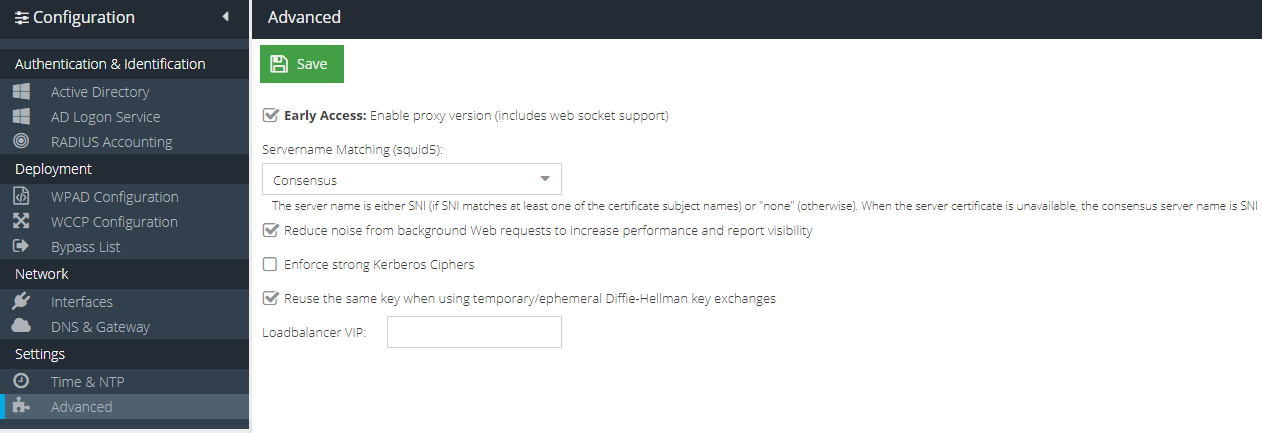
Enable proxy version (includes web socket support)
This option configures the USS Gateway proxy to use squid5.
Servername Matching (squid5)
This operation mode determines how the server name is identified in HTTPS connections. The default mode is consensus.
Consensus | The server name is either SNI (if SNI matches at least one of the certificate subject names) or "none" (otherwise). When the server certificate is unavailable, the consensus server name is SNI. |
Client Requested | The server name is SNI regardless of what the server says. |
Server Provided | The server name(s) are the certificate subject name(s), regardless of what the client has requested. If the server certificate is unavailable, then the name is "none". |
Reduce noise from background Web requests to increase performance and report visibility
Many modern websites, particularly Search Engines and Mapping sites, use lots of background web requests to suggest terms and locations. On a large network with many users, this can add up to a significant amount of extra processing and log entries, which provide little benefit. This options filters the out these types of request, which should increase performance and also reduce the noise visible in the Web Security reports.
Enforce strong Kerberos Ciphers
Prevents the authentication protocol from using weak 128bit ciphers to improve authentication security.
Reuse the same key when using temporary/ephemeral Diffie-Hellman key exchanges
Creating a key for every new Diffie-Hellman handshake is the most secure method, but the key creation is CPU- and disk-intensive which creates additional overhead. On very large networks, this can cause gateway resources to be consumed very quickly. This option can be used to toggle the new key creation mode to suit your requirements.
Loadbalancer VIP
See Configuring USS Gateway to work with LoadBalancer.org software load balancer